Managed threat detection and response
FAQ
Managed Detection and Response (MDR) is a comprehensive cybersecurity service that provides continuous monitoring, detection, investigation, and response to threats in real-time. MDR combines advanced technologies, such as threat intelligence, behavioral analytics, and machine learning, with human expertise to proactively detect and respond to cyber threats.
MDR services are typically offered by third-party security providers, who use a combination of specialized tools and a team of security experts to monitor an organization's network, endpoints, and cloud environments. The MDR team works around the clock to identify and investigate suspicious activity, prioritize incidents, and provide actionable guidance to contain and mitigate threats.
MDR services can help organizations detect and respond to a wide range of cyber threats, including malware, ransomware, phishing attacks, data breaches, and insider threats. By outsourcing their security monitoring and incident response to an MDR provider, organizations can improve their security posture, reduce their risk of cyberattacks, and free up their internal resources to focus on core business activities.
Managed Detection and Response (MDR) is important for several reasons:
- Proactive threat detection: MDR provides continuous monitoring and threat detection in real-time, allowing security teams to identify and respond to threats before they can cause significant damage to an organization's systems, data, or reputation.
- Expertise and resources: MDR services provide access to a team of experienced security experts and specialized tools that many organizations may not have in-house. This allows organizations to benefit from the latest threat intelligence and technologies without having to invest in expensive security tools and personnel.
- Quick response time: MDR providers typically offer 24/7 monitoring and rapid incident response times, which can be critical in mitigating the impact of a security breach or cyberattack.
- Cost-effective: MDR can be a cost-effective solution for organizations looking to improve their security posture. Instead of investing in expensive security tools and personnel, organizations can outsource their security monitoring and incident response to an MDR provider.
- Compliance requirements: Many industries are subject to regulatory compliance requirements that mandate specific security measures, such as monitoring and incident response. MDR services can help organizations meet these requirements and avoid costly fines and penalties.
Managed Detection and Response (MDR) offers several key benefits:
- Enhanced threat detection and response: MDR services provide continuous monitoring and real-time threat detection, enabling security teams to swiftly identify and address potential threats before they cause significant harm.
- Access to specialized expertise and tools: MDR providers employ skilled security experts and utilize advanced tools and technologies to monitor networks, endpoints, and cloud environments. This level of expertise and technology can be costly for organizations to develop and maintain in-house.
- Rapid incident response: With 24/7 monitoring and quick incident response times, MDR providers can significantly minimize the impact of security breaches or cyberattacks.
- Cost-effective solution: MDR services offer a cost-effective alternative to investing in expensive security tools and personnel. Organizations can leverage the latest threat intelligence and technologies without substantial capital investments.
- Compliance assistance: Many industries must adhere to regulatory compliance requirements that mandate specific security measures. MDR services can help organizations meet these requirements and avoid costly fines and penalties.
- Improved visibility and control: MDR services provide organizations with better insight into their security posture, allowing them to identify potential vulnerabilities and implement proactive risk mitigation measures.
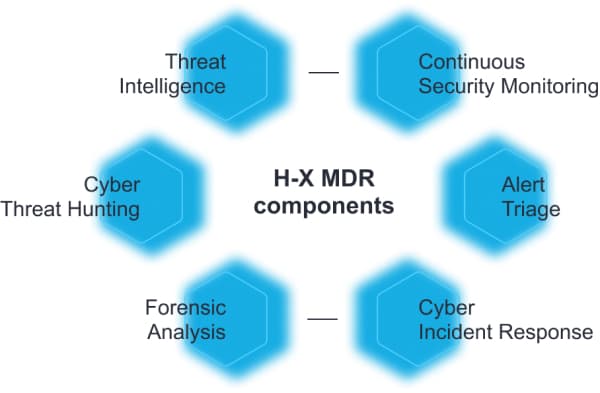
Managed Detection and Response (MDR) services are a comprehensive cybersecurity solution that provides continuous monitoring, threat detection, investigation, and response to security incidents. MDR services typically include the following components:
- Monitoring: Continuous real-time surveillance of an organization's network, endpoints, and cloud environments for potential security threats. This often involves advanced technologies such as threat intelligence, behavioral analytics, and machine learning.
- Threat Detection: Utilization of specialized tools and expertise to analyze and investigate potential security incidents, including the identification of suspicious activities and anomalies that may indicate security threats.
- Incident Response: Provision of rapid response capabilities, including containment and remediation of potential security incidents. This includes offering actionable guidance to organizations on mitigating the impact of security breaches or cyberattacks.
- Forensic Analysis: Conducting detailed investigations of security incidents to determine the root cause and extent of the attack. This helps organizations understand how the incident occurred and prevent similar future attacks.
- Reporting and Analytics: Delivery of comprehensive reports and analytics on potential security incidents, including threat nature, response actions taken, and recommendations for future improvements.
These components work together to provide organizations with a robust, proactive approach to cybersecurity management.
Managed Detection and Response (MDR) services operate by integrating advanced technologies with human expertise to provide continuous monitoring of an organization's network, endpoints, and cloud environments. The process typically includes:
- Data Collection: MDR services gather data from various sources, including network logs, endpoint data, and cloud logs.
- Data Analysis: Specialized tools and technologies, such as threat intelligence, behavioral analytics, and machine learning algorithms, are used to analyze the collected data for potential security threats.
- Threat Detection: The results of the data analysis are used to identify potential security threats, including malware infections, phishing attacks, and insider threats.
- Incident Response: MDR services offer rapid incident response capabilities, including containment and remediation of potential security incidents. This involves providing actionable guidance to organizations on mitigating the impact of security breaches or cyberattacks.
- Forensic Analysis: Detailed investigations of security incidents are conducted to determine the root cause and extent of the attack. This helps organizations understand how the incident occurred and prevent similar future attacks.
- Reporting and Analytics: Comprehensive reports and analytics on potential security incidents are provided, including the nature of the threat, response actions taken, and recommendations for future improvements.
The cost of Managed Detection and Response (MDR) services can vary significantly based on several factors:
- Organization Size: Larger organizations with more complex IT environments typically incur higher costs.
- IT Environment Complexity: More complex environments require more sophisticated monitoring and response capabilities.
- Service Level: The depth and breadth of services required will impact the cost.
- Scope of MDR Solution: The number of endpoints, devices, and services that need monitoring affects the overall cost.
MDR services are usually priced on a monthly or annual subscription model and may include:
- Implementation Costs: Initial setup and configuration of the monitoring and detection infrastructure. This can vary based on the complexity of the IT environment and the number of endpoints and devices to be monitored.
- Subscription Fees: Ongoing costs for the monitoring and detection infrastructure, security monitoring tools, and continuous support and maintenance. These fees may be based on the number of monitored endpoints, devices, and services.
- Incident Response Costs: Often charged on a per-incident basis, varying with the severity and complexity of each incident.
Due to the variability in pricing, organizations should request detailed quotes from MDR providers based on their specific needs and IT environment. It's also advisable to compare offerings from multiple providers to ensure the best value for the required level of security.