The consequences of neglecting to audit smart contracts, applications, and blockchain protocols
In this article, you will learn about the biggest incidents in DeFi due to mistakes made by developers, owners, and users of smart contracts and DApps. It turns out that the growth rate of crypto crime is more than 5 times that of cybercrime in general. How to avoid millions in losses? There are simple and reliable solutions.
DeFi’s missing billions

According to Crystal Blockchain’s latest report on cryptocurrency security breaches and fraud over the past 11 years, asset owners have lost USD 14.7 billion in cryptocurrency since 2011 due to hacking and fraud. The main arena of crypto crime has been the DeFi (Decentralised Finance) ecosystem, i.e. financial instruments created on the blockchain.
The table below shows the number of crypto crimes and the amount of damage caused in recent years.
| Year | Number of incidents | Amount of damage, mln. USD |
| 2011 | 8 | 1,04 |
| 2012 | 14 | 5,76 |
| 2013 | 16 | 14,2 |
| 2014 | 11 | 646 |
| 2015 | 10 | 400 |
| 2016 | 5 | 147 |
| 2017 | 14 | 634 |
| 2018 | 15 | 974 |
| 2019 | 26 | 3500 |
| 2020 | 31 | 1520 |
| 2021 | 94 | 4632 |
| 2022 | 120 | 2218 |
Over the years, criminals committed 167 DeFi hacks, 123 security attacks, and 74 fraud schemes. Criminals stole more than USD 3.2 billion after hacking centralised platforms. The hackers have stolen more than USD 4 billion from DeFi projects due to their vulnerabilities. The rest of the funds were stolen by fraudsters from various projects, systems and platforms, not using technical vulnerabilities, but by abusing users’ trust.
Since 2021, the attention of hackers has shifted noticeably to DeFi. Since 2022, decentralized projects have already been hacked 20 times more often than centralized projects. Below is a chart of the total damage from various types of crypto crimes by year.
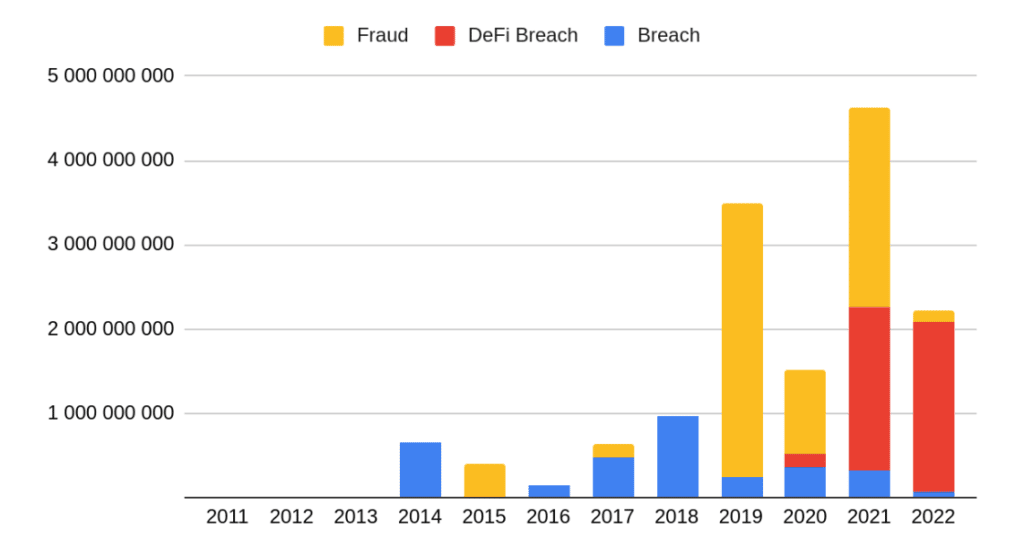
According to experts, the attacks on DeFi projects have increased so much because the sector has been developing rapidly. Projects are rushing to market with insufficient testing and security audits.
According to the report by Leonardo, the volume of all cybercrime (not only crypto crime) losses reached USD 6 trillion in 2021. Curiously, this figure matches the Cybersecurity Ventures forecast that was published in 2020.
The average growth rate of cybercrime losses over the last 5-7 years is about 15% annually. Meanwhile, based on Crystal Blockchain’s statistics, the average growth rate of crypto crime damage over the same time period is more than 80% annually.
Thus, the average annual growth rate of cryptocurrency thefts is more than 5 times higher than the average annual growth rate of damage from all cybercrime.
The consequences of neglecting security auditing

Smart contracts are the central element of the DeFi ecosystem. Thanks to their technology, decentralised applications (DApps), which can control user funds without an intermediary, are being actively developed. However, unaudited smart contracts almost always have many vulnerabilities and other flaws that can negatively impact DeFi’s security. In other words, if your smart contract is vulnerable, so is your DeFi application.
Since smart contracts, like any other software, are developed by humans, the human factor is crucial. Regardless of the professionalism and experience of the developer, the risks of making mistakes in code and configurations always exist. This is why a large proportion of smart contracts are not immune to hacking. In such cases, criminals exploit bugs or flaws in the code of smart contracts to carry out malicious actions.
Here are some examples of recent major incidents in the cryptocurrency industry involving mistakes by developers, owners, and users of smart contracts, distributed applications and protocols.
Ronin Network Sidechain. This hack is the biggest in the history of the DeFi segment so far, and it serves as a prime example of a crypto incident. We wrote about it in more detail right after it occurred. The Ronin Network platform associated with the popular play-to-earn “Axie Infinity” game lost USD 625 million in March 2022 as a result of a hacking attack on a service loophole that the developers had opened for free transactions by their affiliates.
Yam Finance protocol. Yam Finance attracted more than 400 million USD in 2020 and then dropped to almost zero. This happened after an error in the project’s unaudited smart contract increased the number of YAM tokens by a factor of 10. This made it impossible to make any management decisions. Due to the lack of code auditing, a single line of code led to the collapse of an entire new promising project, and that happened in some other DeFi smart contracts too.
Wormhole platform. In February 2022, cryptocurrency platform Wormhole patched security vulnerabilities, and published the patches, but did not have time to apply them. An unknown attacker discovered a zero-day vulnerability in the platform’s code and exploited it. By forging a valid signature, the hacker was able to complete the transaction and obtain USD 325 million in Ether.
Nomad Bridge. More recently, in early August 2022, the Nomad Bridge was breached. The damage amounted to USD 190 million. The reason for the hack was a small inaccuracy in the code. The Nomad smart contract failed to properly verify the transaction when it was entered.
Qubit Finance platform. This hack is similar to that of the Wormhole platform, and it happened at around the same time. A hacker stole around USD 80 million in BNB cryptocurrency from the platform’s wallet by exploiting a vulnerability in one of the contracts that the company used for user transaction processing.
Blockchain platform Solana. The incident took place in August 2022. Hackers hacked into about 8,000 Solana-based wallets, gaining access to the wallet holders’ funds. The transactions were signed on behalf of the users. The loss was estimated by experts at USD 8 million.
Metamask. A top ten Degen Score user lost about USD 500,000 in USDC in August 2022 due to an exploit and a permit-function. This feature had been conceived initially to improve the convenience of Ethereum users. The attacker fraudulently obtained the victim’s electronic signature and sent a transaction with the permit-function with that signature. This preparation gave the malicious smart contract the ability to control all the funds in the victim’s wallet. The malicious smart contract then called the transferFrom function, which stole all the funds. What makes this incident noteworthy is that this time the smart contract was not a vulnerability, but a threat. Also, the victim here was not a project, but an individual cryptocurrency wallet. It is unlikely that any of you would want to be in that wallet’s user’s shoes and lose your money.
Other major DeFi hacks of the current year are Beanstalk (USD 182 million stolen in ETH, ERC20), Maiar Exchange (Elrond, USD 113 million stolen in ETH, ERC20 in EGLD), Harmony (USD 100 million stolen in ERC20), Mirror Protocol (USD 90 million stolen in TERRA) and Rari Capital (USD 80 million stolen in ETH).
“Decentralised” does not mean “secure”

DeFi, smart contracts and blockchain protocols are being compromised more and more often, at an exponential rate. Vulnerabilities, or simply put, bugs in the code and security flaws lead to huge financial losses. One of the main causes of financial losses is the neglect of smart contract audits.
Application and protocol developers make mistakes just as often as smart contract developers. Many DeFi smart contracts, protocols, and applications are created by mindlessly copying code that is not always appropriate for specific cases. This potentially increases the security risks of your projects.
Many mistakes are made by blockchain users who trust unreliable projects, which then become rug-pulls and other scams. By the way, fraud is a big topic of its own, which we will certainly cover in a future article.
Launching or deploying an unaudited smart contract, ignoring code security checks, and ignoring pentests will sooner or later lead to unfortunate consequences. The specific nature of security incidents is that they occur quite unexpectedly. Theft of funds, manipulation of assets, malfunctions and other vulnerabilities of all kinds can bring your blockchain project to ruin as soon as it takes off, or later when it hurts, even more, to fall from a great height.
Fortunately, however, Web3 risks are manageable. First, developers of Web2- and Web3-applications and protocols have the opportunity to improve the security of their projects by outsourcing source code audit to specialized companies.
Second, applications need to be deployed and maintained properly. Even a fully secure and properly audited application can be deployed incorrectly, in an unsuitable, outdated, or misconfigured environment. Therefore, we recommend complementing source code audits with penetration testing in test and production environments, as well as with cloud audits.
Finally, you may not know in advance how much money your smart contract can manage, or how much money you will raise on the ICO. However, once your smart contract is published, you will no longer be able to fix it. Therefore, in order to avoid huge losses or lost profits, we strongly recommend auditing your smart contracts in advance and properly.
Even if you are confident in the competence of your developers, DevOps and security specialists, the cost is too high. So insure yourself extra and take advantage of our security services, which, among other things, also include training your professionals, certifying your company, monitoring security events, investigating security incidents, and much more.
You have spent your time reading our article, we appreciate it and will try to make up for it. Take advantage of our bonus for you, valid within four weeks after your request, of a free one-to-one consultation on any cryptocurrency security issues and other Web3 systems.
Subscribe to our Telegram channel so you do not miss new articles on our blog.
