Top mind-blowing powerful blockchain incidents involving hacking attacks

We have recently written about the frightening statistics of major blockchain incidents and the explosion of cryptocurrency thefts. We highlighted the hacks of DeFi – the distributed financial instruments.
Today, we want to draw your attention to hacking attacks on centralised crypto exchanges, funds, and other blockchain financial institutions, as well as a fresh trend in recent months – blockchain bridge hacks.
You may find this article interesting or useful if you work with one of these exchanges or organisations, or if you use such bridges. Please pay special attention to our overview and recommendations if you plan to develop, implement, or purchase such technologies.
In this article, we have compiled the most “high-profile” blockchain hacking incidents of the past 11 years. Unauthorised access to digital assets, detective stories, colossal amounts of damage, predictions, and, finally, robust solutions to secure against hacking – read about it all below.
Major cryptocurrency hacking incidents

The following are prime examples of major incidents in the cryptocurrency industry involving hacking attacks on cryptocurrency exchanges and other centralised organisations operating in the blockchain industry.
Mt.Gox
Mt.Gox is a cryptocurrency exchange that was based in Tokyo. Mt.Gox began operations in 2010, but declared bankruptcy as soon as 2014. Successful hacking attacks on the exchange continued throughout its lifetime until this exchange was finally destroyed.
At its peak, Mt.Gox was considered the world’s largest bitcoin exchange, becoming a popular target for hackers. In 2011, hackers used stolen customer credentials to transfer bitcoins. In the same year, several thousand bitcoins were “lost” due to flaws in network protocols. Customers expressed dissatisfaction with the exchange, noting withdrawal problems.
Technical errors and uncertainties in the code prevented the company from getting a clear view of transactions. However, in early February 2014, the company did detect suspicious activity in its digital wallets. The exchange then suspended withdrawals, after suffering huge losses. Reports on the number of bitcoins lost ranged from 650,000 to 850,000 coins, totalling around USD 615 million. Some of the lost BTC coins belonged to the company and the rest to users.
Coincheck
The Mt.Gox example taught little to other exchanges, even within Japan alone. The year 2018 was particularly “fruitful” for hackers.
Coincheck is one of Japan’s largest digital currency exchanges. In January 2018, Coincheck claimed to have lost around USD 535 million in virtual assets due to a hacking attack on its network. The reason for the hack was cited as storing coins in a vulnerable “hot wallet”. Such wallets are connected to the Internet and are always more vulnerable than “cold wallets”.
Coincheck executives commented on the catastrophic security lapse, citing technical difficulties and staff shortages.
This hack has noticeably shaken the confidence of many users and companies in crypto and blockchain security protocols, forcing other exchanges to pay due attention to their security protocols to protect assets from similar incidents.
KuCoin
KuCoin is a cryptocurrency exchange in Asia headquartered in Singapore. KuCoin claimed in September 2020 that attackers hacked into its systems and completely emptied its “hot wallets”. The company suffered a loss of USD 281 million.
During the investigation into the incident, it emerged that one or more hackers had managed to obtain the private keys to the exchange’s “hot wallets”. The attackers gained control of a huge amount of BTC, ETH, XRP and ERC20 TOKENS. According to CEO Johnny Liu, KuCoin moved the remaining funds to new “hot wallets”, abandoned the old ones, and froze customer deposits and withdrawals.
Bitmart
Bitmart is a cryptocurrency trading platform. In December 2021, the exchange experienced a large-scale security breach. Hackers managed to withdraw tokens worth around USD 150 million.
The exchange said the security breach was mainly caused by a stolen private key that affected “hot wallets”. Hackers systematically used the aggregator of 1inch decentralised exchange (DEX) to exchange stolen assets for Ether (ETH) and used a secondary address to enter ETH into the Tornado Cash privacy mixer, making it difficult to trace the hacked funds.
IRA Financial
IRA Financial is a US-based pension fund investing in the cryptocurrency industry. In February 2022, hackers stole USD 36 million (USD 21 million in BTC and USD 15 million in ETH) from the fund’s pension accounts.
IRA Financial was linked to Gemini, a cryptocurrency exchange set up by the Winklevoss twin sportsmen, who also famously sued Mark Zuckerberg for stealing the idea for the Facebook social network.
As the investigation into the incident revealed, on the day of the incident, the attackers made a false call to the police, who arrived at the IRA office and distracted employees from monitoring transaction security.
There were also serious security lapses in Gemini Exchange’s processes and systems. The company’s protocols were flawed and contained a massive vulnerability that allowed a single customer account to be compromised to give a hacker access to all IRA customer accounts.
Crypto.com
Crypto.com is a cryptocurrency exchange company based in Singapore. Crypto.com reached out to us in late 2021 but never took advantage of our cybersecurity services, and already in January 2022 suffered massive losses. Hackers broke into about 500 user accounts of the company and gained unauthorized funds in the amount of 4,836.26 ETH, 443.93 BTC and about USD 66,200 in other currencies. According to the exchange rate at the time of the incident, the damage amounted to USD 15.3 million in ETH and USD 18.7 million in BTC, with a total of USD 34 million in losses.
Crypto.com became aware of the cyberattack after the company’s risk monitoring systems detected a few users making unauthorised cryptocurrency withdrawals from their accounts.
We deliberately do not focus on these companies’ response to their hacks, because we encourage preventing incidents rather than dealing with their consequences. It is always more beneficial to build security from an earlier stage, i.e. developing a secure architecture and security controls across all stages of business processes: from user verification to anomaly monitoring, from supply chain security to automatic monitoring of technical vulnerabilities during software testing.
Major hacks of bridging protocols

A blockchain bridge is a protocol that ensures the compatibility and interoperability of two blockchains. With a blockchain bridge, it is possible to transfer assets conveniently from one blockchain ecosystem to another without selling cryptocurrency.
Blockchain bridges have many advantages, but there are also disadvantages. The examples in the chart below illustrate the frequency of bridge hacks in 2022 due to the lack of proper protocol security.
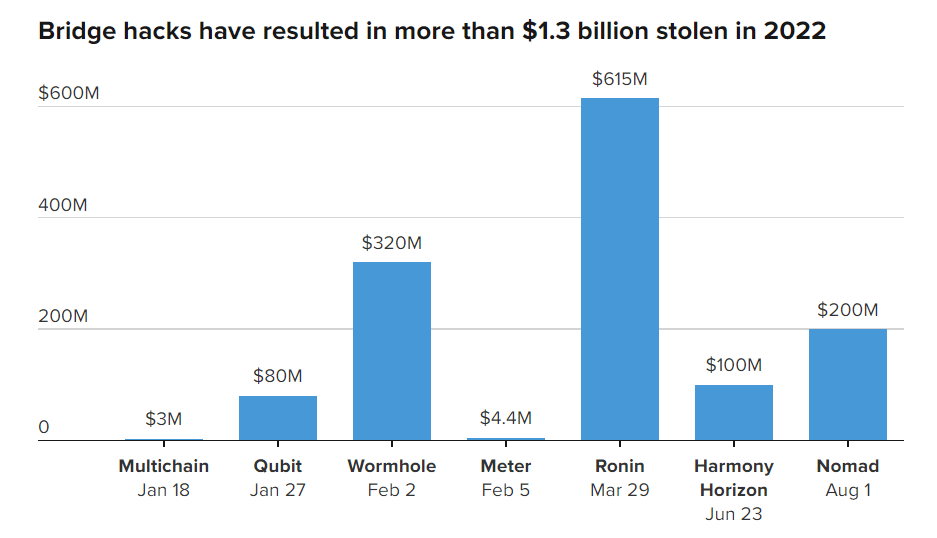
According to analyst firm Chainalysis, about USD 1.4 billion was lost as a result of bridge hacks between January 1 and August 2 in 2022.
The biggest event this year was the Ronin incident in March. Hackers hacked a bridge that supported a popular game with non-fungible Axie Infinity tokens to the tune of USD 625 million.
Also in February 2022, the Wormhole crypto bridge was hacked. The total loss amounted to around USD 320 million.
In addition, Harmony’s Horizon bridge was attacked in June this year. Hackers managed to steal USD 100 million. And about a month ago, crypto criminals stole nearly USD 200 million in the Nomad cross-chain bridge hack.
According to Chainalysis, the sum stolen in blockchain bridge hacks accounts for 69% of the money stolen in cryptocurrency-related hacks in 2022.
Thus, we can see that numerous hacks of crypto exchanges have taught them over the years to pay more attention to security after all. That security has not become perfect, but it has grown so much that hackers have started to switch to easier targets.
Next year, 2023, we are likely to see even brighter and bigger DeFi and cryptocurrency bridge hacks. Bridges and DeFi are relatively new technologies and, like exchanges in their time, they have yet to go through a painful path of hacks to improve their security.
How to keep cryptocurrency secure from hacks

As we have seen above, the technical and organisational flaws in blockchain networks and associated ecosystems can be extremely costly, and lead to most unfortunate consequences.
Fortunately, we have ready-made solutions to help you avoid falling victim to these cybercrimes and your programmers’ mistakes. You need to find and fix vulnerabilities and other security flaws in advance to drastically reduce the risks of hacking attacks and breaches, and the loss of large sums of money.
- Crypto wallets security recommendations and cryptocurrency operation instructions are useful not only for those who are familiar with cryptocurrencies, but also for those who are just getting acquainted with them.
- Source code audit of software is essential for its developers, owners and buyers. We successfully find not only known security issues, but also zero-day vulnerabilities and problems in business logic. In doing so, we effectively analyse not only blockchain-based software, but also traditional distributed and centralised applications, web applications, mobile applications, etc.
- Penetration testing is essential for any online service or software owner who wants to simulate hacker actions and check how successful they could be.
- Cloud auditing is conducted to ensure that even the most robust, audited and tested software will not appear to be vulnerable due to issues in configuration and hosting policies.
- Smart contract auditing is a service similar to software code analysis, only in this case the software is the smart contracts, a key element of DeFi. We pay a lot of attention to vulnerabilities and security analysis tools for smart contracts.
You have spent your time reading our article, we appreciate it and will try to make up for it. Take advantage of our bonus for you, valid for the next four weeks, namely a free one-to-one consultation on any security issues with cryptocurrency solutions and other Web3 systems. Please use the promo-code “2022-09-BLOCKCHAIN-TOP” in the contact form. We can quickly help you determine which security methods and tools you currently need the most.
Please, use our free online security scanner to get an idea of the vulnerabilities of your website.
Subscribe to our Telegram channel to make sure you do not miss any new articles on our blog.
