Cyber Attacks 2022-2023: Overview of The Biggest Incidents, and What Awaits Us in 2024
In the world of high technologies, not only the scope of opportunities is growing but also the threats that can disrupt digital life and privacy. It can cause millions of dollars in damages and ruin businesses built over years.
We will examine the largest cyber attacks of 2022 and 2023, the threats, their trends over the past years. Also, we will forecast for 2024 and offer solutions to protect your digital life and business.
The biggest cyber incidents of 2022 and 2023
The number of cyber attacks and cybercriminals worldwide is growing rapidly. They cooperate, form large criminal corporations, adapt to new changes, look for new opportunities, and employ increasingly sophisticated attack models. Ransomware attacks and unauthorized data access (data breaches) are the most common among all cyber incidents in the past few years.
At the same time, these and other incidents are interconnected in peculiar technological processes and life cycles. For example, cybercriminals use data leaks for further attacks, including ransomware attacks. Then their owners allocate funds to finance spyware and other malicious applications, botnets, and attacks of other kinds.
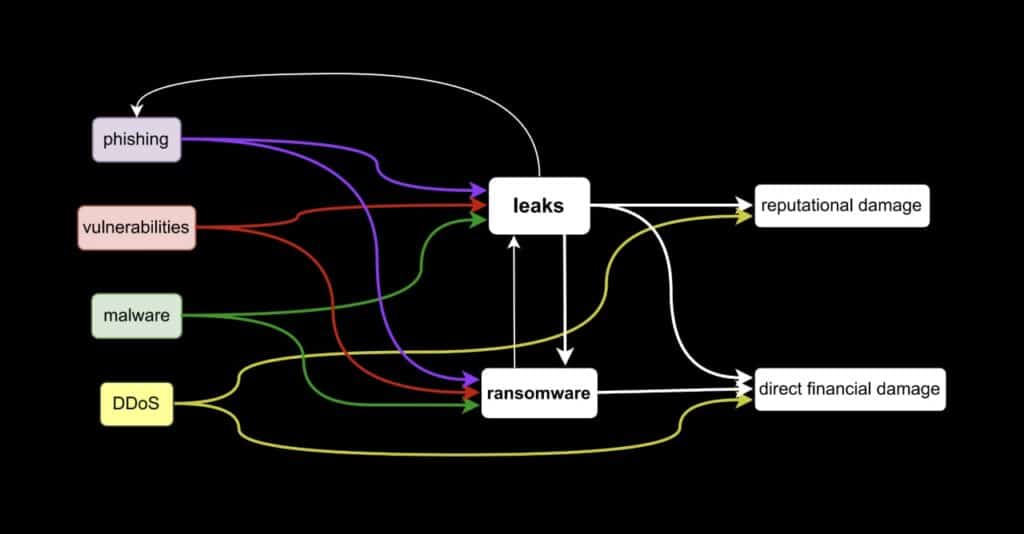
In 2022 and 2023, striking cyber crimes occurred on a massive scale, costing companies and countries billions of dollars. We have gathered information about the most damaging cyber attacks of 2022 and 2023.
Major victims of cyber attacks in 2022 and 2023
| A victim of a cyber attack | Consequences |
| 2022 | |
| Costa Rica | losses amount to 1.3 billion USD (30 million USD per day for one and a half months) |
| Axie Infinity (Ronin Network) | 600 million USD were stolen |
| Binance | 570 million USD were stolen |
| Wormhole token bridge | 321 million USD were stolen |
| Common Spirit Health | losses amount to 160 million USD |
| Medibank | the company’s losses for 2022 and 2023 are $46.4 million, and the projected losses will reach $80 million |
| Neopet | personal information of 69 million people was stolen |
| personal information of 5.4 million users was stolen | |
| Advocate Aurora Health | personal information of 3 million patients was stolen |
| Optus | the identification numbers of 2.1 million customers were exposed |
| Red Cross | 515,000 people’s personal information, including their location, was stolen |
| The Portuguese Ministry of National Defense | confidential NATO documents were stolen |
| Airport websites | the websites of 23 airports in the USA, Japan, Estonia and Lithuania were hacked |
| 2023 | |
| MOVEit | 2393 organizations and approximately 69 to 73.8 million people were affected by the information leak |
| DarkBeam | over 3.8 billion user email accounts with passwords have been stolen |
| 23andMe | potentially millions of DNA datasets have been stolen (exact quantity undetermined) |
| Johnson Controls International | more than 27 TB of corporate data was stolen and the company’s VMWare ESXi virtual machines were encrypted |
| Barts Health NHS Data Breach | 7 TB of data leaked |
| Tampa General Hospital | medical data of 1.2 million patients were stolen |
Who and how are most affected by cybercriminals?
The financial, healthcare, IT and public sector industries were the most affected. 2023 is becoming another record year for ransomware. Their reported number has increased by 49% compared to 2022. At the same time, it is unknown how many undetected attacks exist or those that are not disclosed for some reason. This year also witnessed a significant number of attacks aimed at data theft.
Ransomware Attacks
The ransomware industry remains one of the primary threats to organizations worldwide. Not only data leaks, data recovery, long-term struggle with the consequences (payments, lawsuits, reputation damage, etc.) bring losses, but also ransom payments to the owners of ransomware applications. Criminals target companies with large volumes of critical data, as there is a high probability that they will pay a ransom to avoid data leaks or losses, and to maintain confidentiality, preventing reputational damage.
In recent years, the number of attacks and organized criminal groups has been increasing, which directly affects the number of cybercrimes.
According to statistical data, there has been a significant increase in ransomware attacks since 2020. The highest spike is observed in the current year, even without considering the 4th quarter. Therefore, the projected number of attacks by the end of 2023 will be more than 800 million.
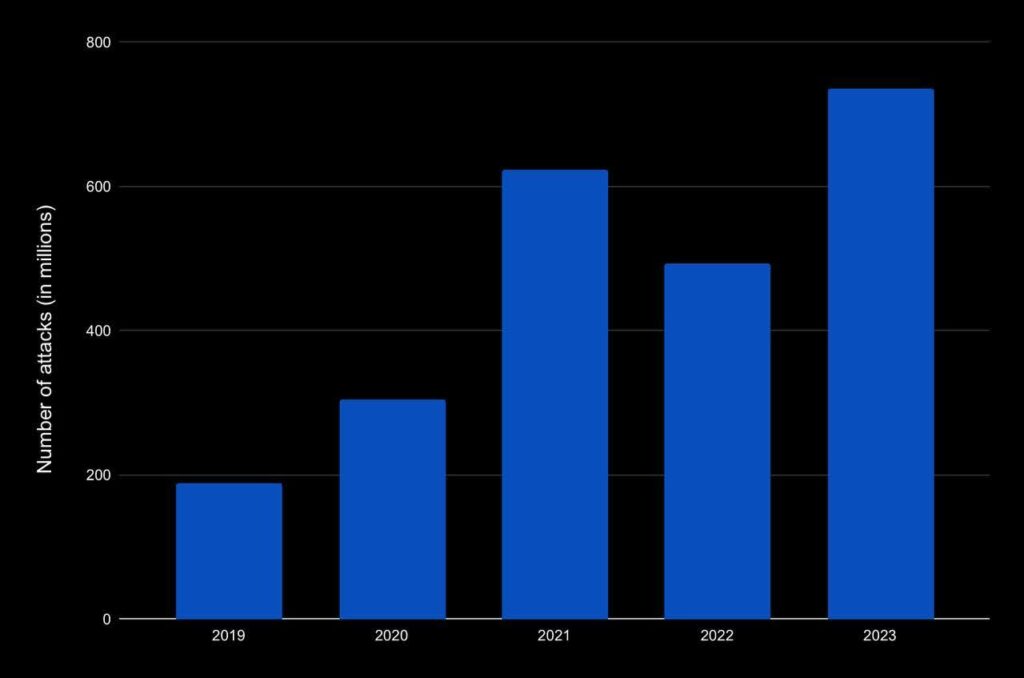
The number of ransomware attacks in 2019-2023
This year, law enforcement agencies have been significantly more active in combating cybercriminals. Unfortunately, this has not prevented and will not prevent this industry from actively developing, creating new groups, and committing more and more ransomware attacks. In 2020 and 2021, the total amount of ransom payments substantially increased, reaching 766 million US dollars, but in 2022 the mark dropped to 457 million. Why so?
In 2020 and 2021, organizations suffered significant losses, creating a need to protect their operations because it became evident that attacks will persist and increase. Several measures helped organizations combat attacks and minimize damage:
1. Creation and restoration of data backups.
2. Cyber insurance.
3. Enhanced cybersecurity measures.
4. Activation of cyber law enforcement.
In the first half of 2023, the total ransom payments amounted to 449 million. Creating backups of data in 2022 and 2023 has become the most widespread approach for data storage and avoiding payments to extortionists. This method was used by 70% of organizations that reported an attack.
What about those organizations that paid the ransom?
Typically, they regain control over their data. Only 1% of victims did not regain access to their information. This shows mostly the strategic thinking of the criminals, who plan to continue their illegal business, so they have to keep their promises.
How long does data recovery take, and what is its cost?
It usually takes up to one week to recover data. This does not depend on the method of recovery (ransom payment or restoration from a backup, if there is one). On average, 40% of organizations recover data within this time frame, 30% within one month, and 18% need 1-3 months.
Average recovery cost for a large organization, excluding ransom payments, was $1.85 million in 2021, $1.4 million in 2022, and the cost in 2023 is expected to be around $1.82 million. These amounts reflect the cost of downtime, including salaries, lost income, and more.
Ransomware as a Service (RaaS)
The rise and continued growth in the number of attacks and organized groups are closely tied to criminals not just conducting attacks but also refining this business. In this case, it’s Ransomware as a Service (RaaS), a business model that has been in existence for over a decade.
How does it work?
Hackers develop ransomware attack models and sell them to affiliates who use these models for real attacks. In the case of a ransom payment to the affiliate, the hacker-developer receives a certain percentage for the service from each ransom.
This is why the number of major ransomware groups has sharply increased:
– 2021: 19 groups;
– 2022: 31 groups;
– 2023: 48 groups.
Additionally, ransomware actors constantly look for new and convenient opportunities for attacks. Over the past years, the most common channels for ransomware attacks have been:
1. Exploiting vulnerabilities.
2. Compromised credentials (leaks).
3. Emails (phishing).
Which industries are the biggest victims of ransomware?
In 2022 and 2023, the most attractive targets for ransomware attacks were the education, construction, manufacturing, logistics, real estate, and government sectors. Hence, it is likely that these industries will suffer the most from ransomware in 2024 as well.
Therefore, in the coming years, the target industries for ransomware will be those with sensitive data, as well as organizations with a weak level of protection.
The most effective protection against cyber extortion is a backup of all critical data. Explore our real-time intercontinental backup solution and schedule a free consultation.
Data breaches
Information leaks have a detrimental impact on businesses not only through financial losses but also through reputation. Organizations suffer from reputational damage and legal consequences. So the most serious problem after an attack is the duration and scope of the consequences, which are quite difficult to determine. According to IBM data, the average cost of a data breach reached a peak in 2023, amounting to 4.45 million dollars. Compared to 2022, when the breach cost was 4.35 million US dollars, the figure increased by 2.3%.
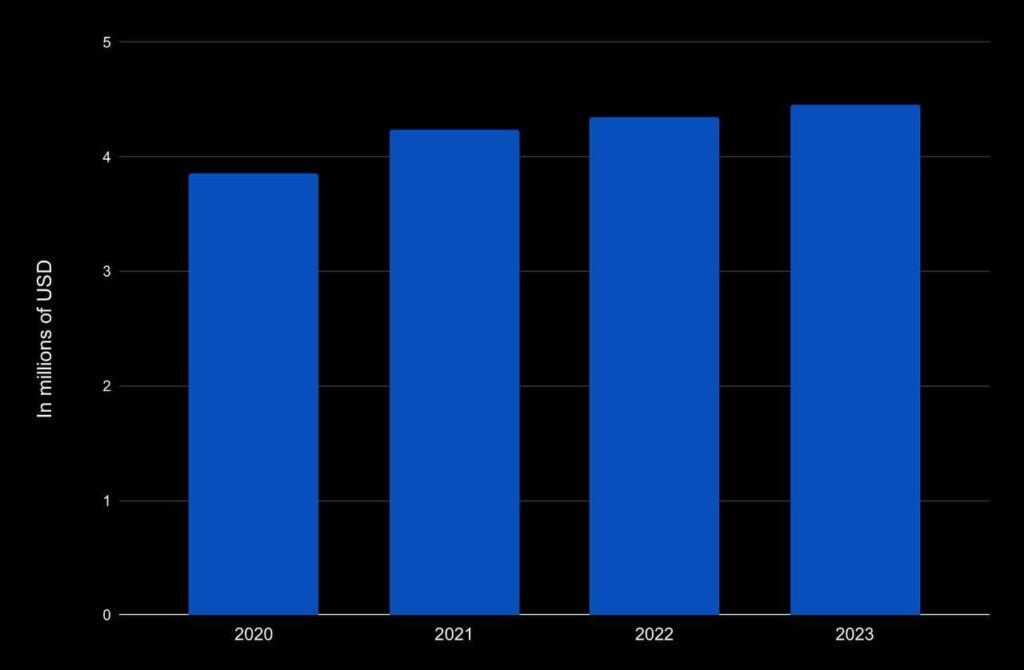
The average cost of damages from a data breach
Will the number and cost of data breaches increase in 2024?
We have reasons to believe that both the number and the damage from data breaches will continue to rise. Analyzing statistical data in recent years, the cost of information leakage is increasing (with a growth rate of 15.3% since 2020). The number of large attacks is also on the rise. In 2020, there had been 1120 of them, and by 2023, the number had increased to 1659. Of course, the increase in the number of breaches also impacts the cost of damages from them.
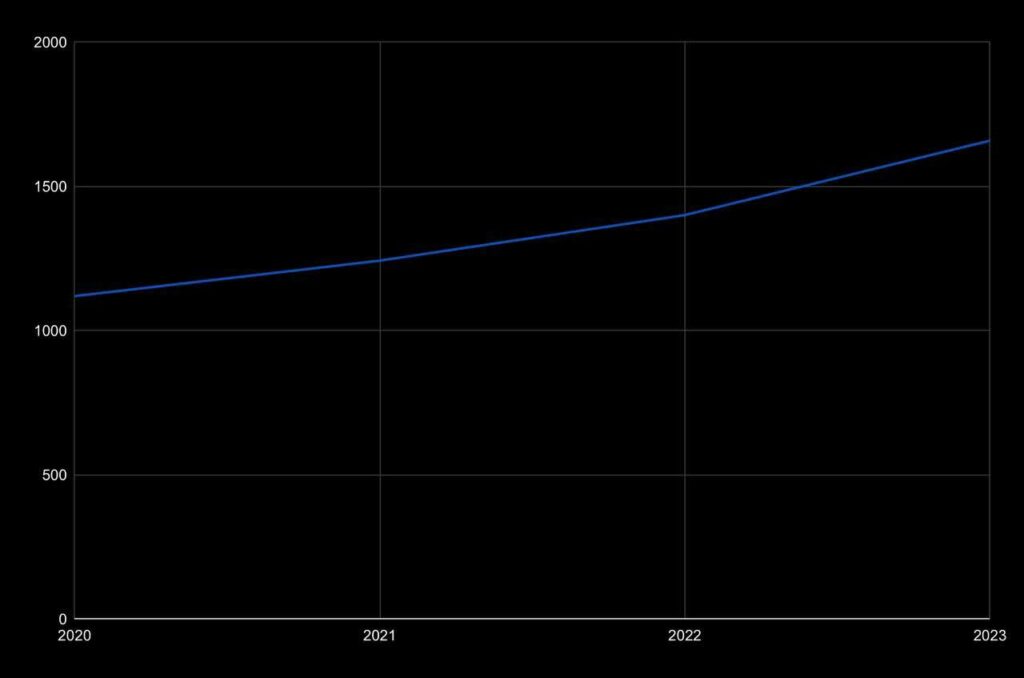
The number of large data breach attacks in 2020-2023
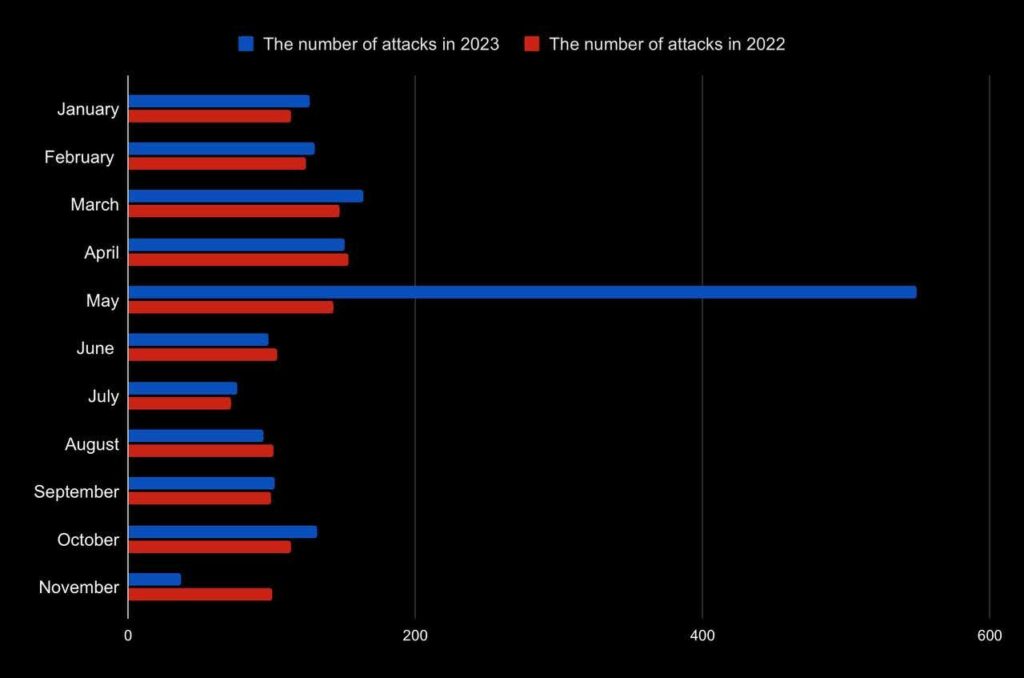
The number of attacks with large data breaches in 2022 and 2023
The number of attacks increased to 1659 by the end of November. Compared to 2022, this is a 10% increase. 2023 stood out with the quantity of May attacks with data leaks, directly impacting the sharp dynamics. However, the overall number of attacks is increasing gradually. It’s worth noting that these charts are based only on known data breaches, as many companies do not disclose such information.
Industries and countries most affected by data breaches
The healthcare sector became the most vulnerable. Data breach losses have increased by 53.3% since 2020, with the average breach damage reaching $10.93 million. The next most attractive targets for this type of attack are the financial, pharmaceutical, and energy industries.
In 2022 and 2023, cyber criminals most frequently targeted the USA and countries in the Middle East. The number of attacks on Canada, Germany, and the United Kingdom decreased, but they still remain among the top five data breach victims.
Duration and methods of detecting data breaches
A distinctive feature of data breaches is their long-term invisibility if the attack’s goal is not ransom. Once a data breach is detected, it takes time to eliminate the breach.
In 2023, it took an average of 204 days to detect and 73 days to remediate the breach, 207 and 70 days in 2022, respectively, and 212 and 75 days in 2021.
How to detect a data breach?
There are three options for detecting unauthorized access to data:
1. Organisation’s and its providers’ security tools and services.
2. Law enforcement agencies and independent security researchers.
3. Criminals themselves (for ransom purposes).
Unfortunately, as of 2023, only 33% of data breaches are detected through the first method. Regardless of the type, industry, structure, etc., organizations should prioritize their security in the coming years, as the number of cybercriminals is increasing, along with the frequency and types of cybercrimes. Preventing potential attacks is a crucial and challenging task, and we will help you to cope with it. The first step is simple — contact us.
Common Types of Cyber Attacks
Cybercriminals use various methods to gain unauthorized access to government, public, and corporate networks and systems, as well as to steal user credentials and other confidential data, or to interrupt business operations. In recent years, the following types of cyber attacks have been common:
1. Phishing Attacks.
2. Malware Attacks.
3. Exploiting Vulnerabilities.
4. DDoS Attacks.
This classification is to some extent conditional, as certain attacks, such as malware attacks, may be combined with phishing or the exploitation of vulnerabilities. Let’s consider these attack types in more detail.
Phishing Attacks
For many years, phishing has been and still is the most widespread form of cybercrime. As of 2023, approximately 3.4 billion phishing emails are sent daily from compromised email accounts, often obtained through previous data breach cyber attacks. For instance, Google blocks around 100 million phishing emails every day. Meanwhile, 200 thousand phishing sites appear on the network every day.
An interesting fact is that 43% of employees neglect cybersecurity measures while working. This is especially true for new employees and those engaged in constant email communication and handling large amounts of information.
Phishing often disguises itself as corporate, business, financial, or Microsoft-related emails. Since 2021, the ideal platform for phishing attacks has been Linkedin (52% of detected attacks), ahead of Facebook (20%) and Twitter (9%).
Analyzing cyber attacks over recent years, it can be concluded that the most attractive targets for phishing attacks are financial institutions, social media, SaaS, and email platforms.
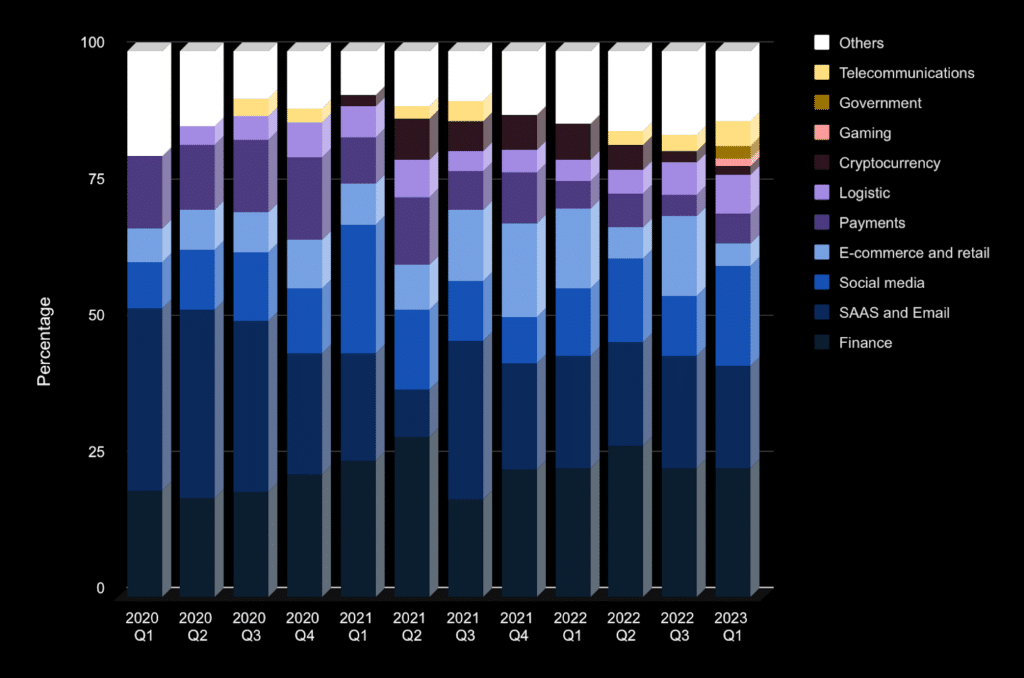
Targets of phishing attacks by quarters from 2020 till 2023
What are the dynamics of phishing in recent years?
Every year, the number of phishing attacks increases. This is attributed to several factors:
1. New IT opportunities that security systems cannot keep up with.
2. The interest from cybercriminals not only in ordinary users, but also in large corporations.
3. The growth in both individual cybercriminals and organized groups.
In 2023, the number of major phishing attacks has notably risen. Data for just the first half of the year has already indicated more significant phishing attacks than the entire year of 2020 and nearly matching the total for 2021.
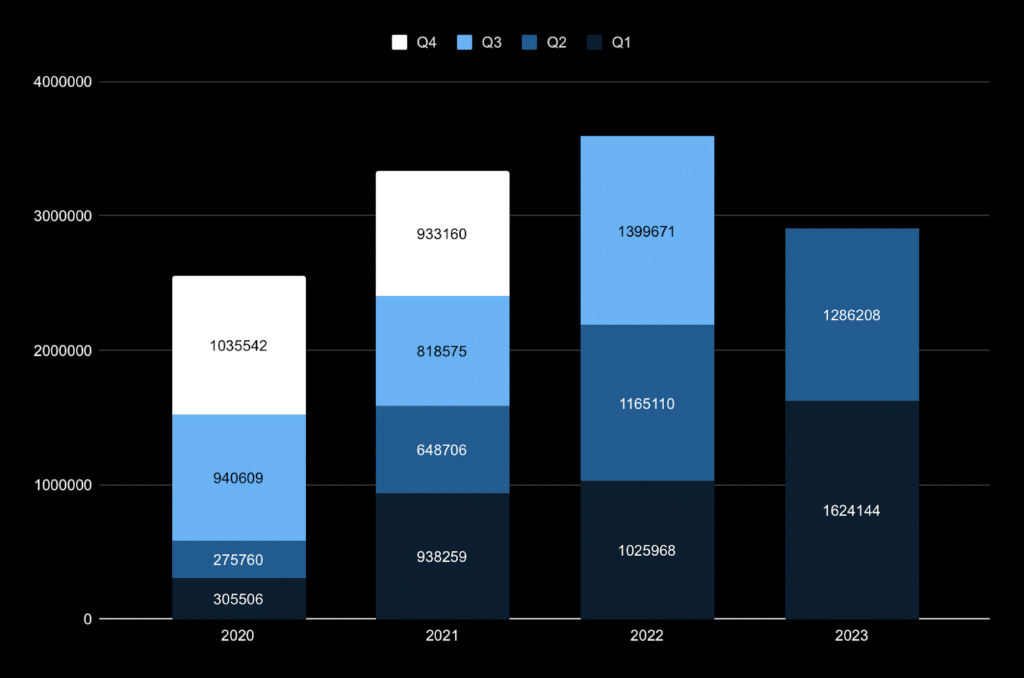
The number of phishing attacks by quarters from 2020 to 2023
It is logical to assume that phishing attacks in 2024 and the following years will be among the most widespread cybercrimes. Their frequency will increase, just like the targets of cybercriminals.
Since 2021, phishing for cryptocurrency theft has been gaining popularity, while conventional payments are less attractive to criminals. In 2023, for the first time, the gaming industry became one of the major targets for attackers. Analyzing statistical data allows us to assert that financial institutions, social media, SaaS, and email will continue to be targeted for phishing in 2024.
So, how can we effectively counter phishing? Firstly, it’s essential to systematically enhance security awareness. Secondly, constantly improve the practical skills in detecting social engineering. Contact us for a free consultation on phishing protection.
Malware attacks
Malware attacks have seen a decline in trend since 2018 when 10.5 billion attacks were recorded. In 2022, their number was halved to 5.5 billion.
Why did this happen? Improved defense mechanisms, cybercriminals switching to simpler methods and easier resources have collectively contributed to the current situation.
But is there cause for celebration? Certainly not. Cybercriminals are not giving up. They evolve, adapt to new realities, and look for better target audiences, among other things.
300,000 new malware programs are discovered daily in 2023. Attackers strike through email in 95% of cases, as well as websites and EXE files. As we constantly search the Internet, visit various sites, and don’t even think about the potential danger, it’s crucial to be aware that threats may be right there. Every week, Google identifies 50 websites containing malicious software.
The highest number of infected computers and their infection rates (the percentage of infected computers out of the total number of computers in each country) are as follows:
– China (47%)
– Turkey (42%)
– Taiwan (39%)
Not only computers but also mobile devices can be infected. Interestingly, Android devices are more vulnerable. The highest level of infection is observed in Iran (30%).
Educational, governmental, military, and medical organizations continue to be the most affected by malware attacks.
It’s noteworthy that Apple’s operating systems, although more secure than Microsoft or Google systems, are not immune to malware, especially spyware.
Exploiting vulnerabilities
Why are vulnerabilities so dangerous, and why do cybersecurity experts increasingly discuss them? The presence of a wide variety of applications installed on computers is a sufficient factor for attackers to find vulnerabilities in these applications, enough to gain unauthorized access. This weakness is an opportunity for cybercriminals to infiltrate the computer systems of organizations and their assets. This leads to significant losses and potential long-term negative consequences for companies. One or two security vulnerabilities can cost a company billions of dollars. That’s why cybersecurity should be a top priority for businesses in the current and upcoming years.
It is clear that cybercriminals choose the targets that are most profitable for them. There are a lot of vulnerabilities. You can check them at the CISA vulnerability catalog. Of course, many experts work on finding and fixing vulnerabilities, but cybercriminals also look for new vulnerabilities continuously to exploit in their future attacks. And this process is ongoing.
We have compiled the most dangerous vulnerabilities as of 2023, with a CVSS score ranging from 9 to 10. These vulnerabilities have already been used in powerful cyberattacks in 2022 and 2023.
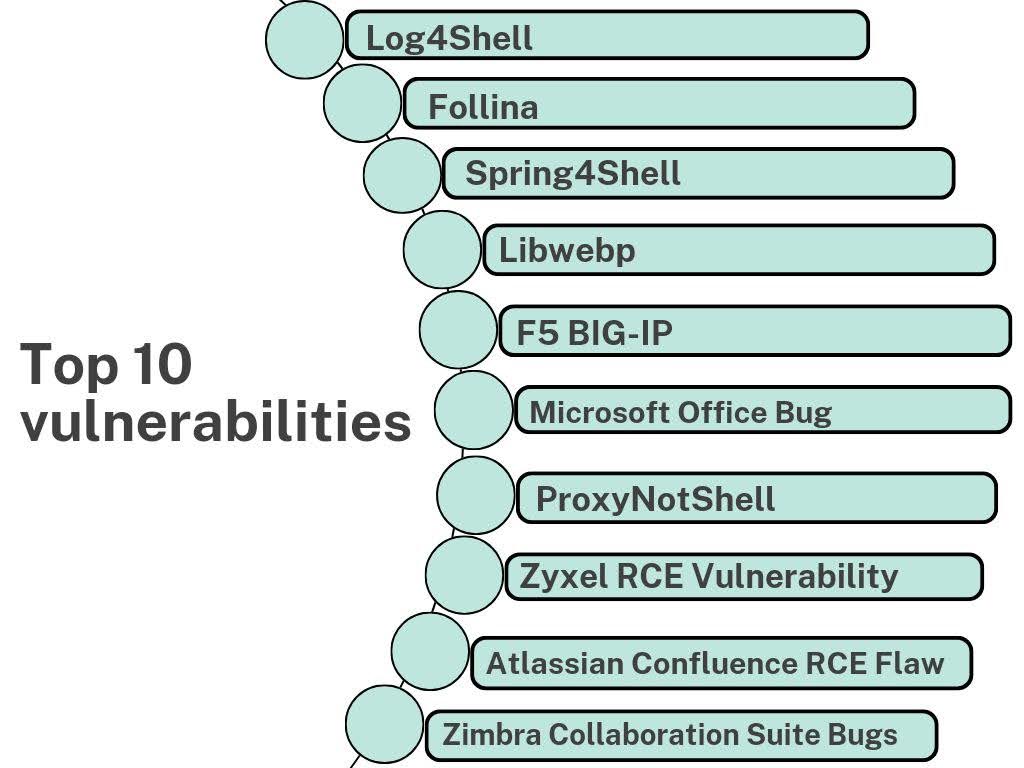
10 most dangerous vulnerabilities of 2022 and 2023
Will these vulnerabilities be used in new cyberattacks? In our opinion, yes.
Will new major vulnerabilities emerge? Definitely.
Can anything be done about it? Ensure a professional security assessment and a strong cybersecurity system for your organization, stay informed, and cultivate personal and corporate security awareness.
DDoS attacks
The essence of DDoS attacks (Distributed Denial of Service) is to disrupt the normal functioning of the target network or server by overwhelming it with large volumes of Internet traffic.
DDoS attacks are becoming increasingly prevalent among cybercriminals. From 2020 to 2023, the number of major attacks increased by 4.6 million, compared to 7.5 million in 2018, which is almost twice as much.
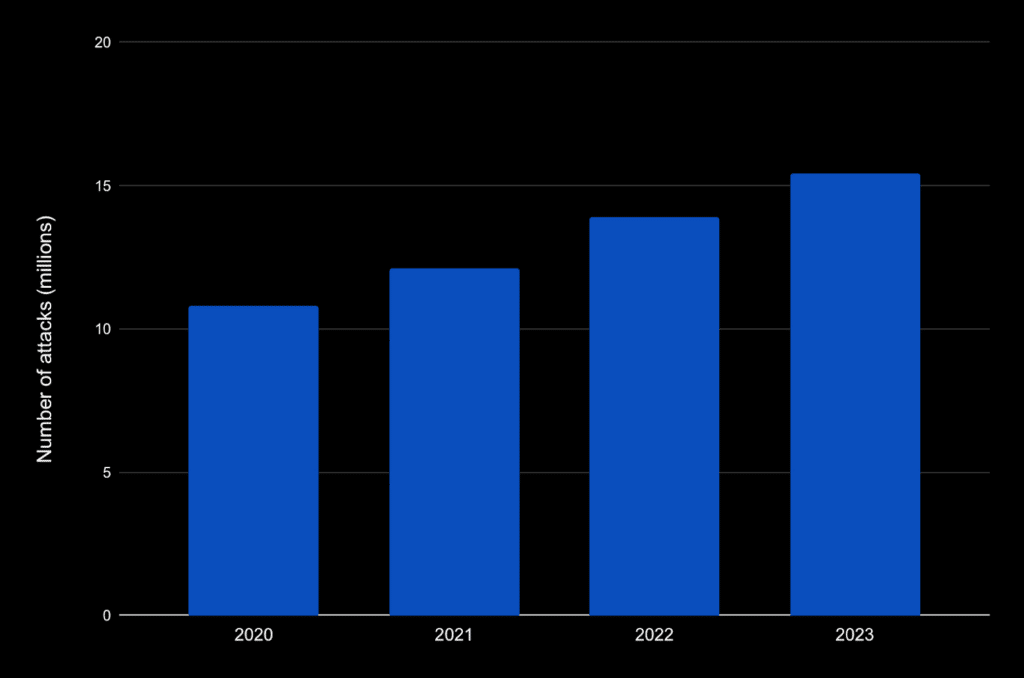
The number of DDoS attacks in 2020-2023
Cybercriminals target various industries, making it impossible to pinpoint one or two specific sectors. Therefore, below, we have depicted the three most targeted industries for each quarter from 2021 to 2023 and their percentage indicators.
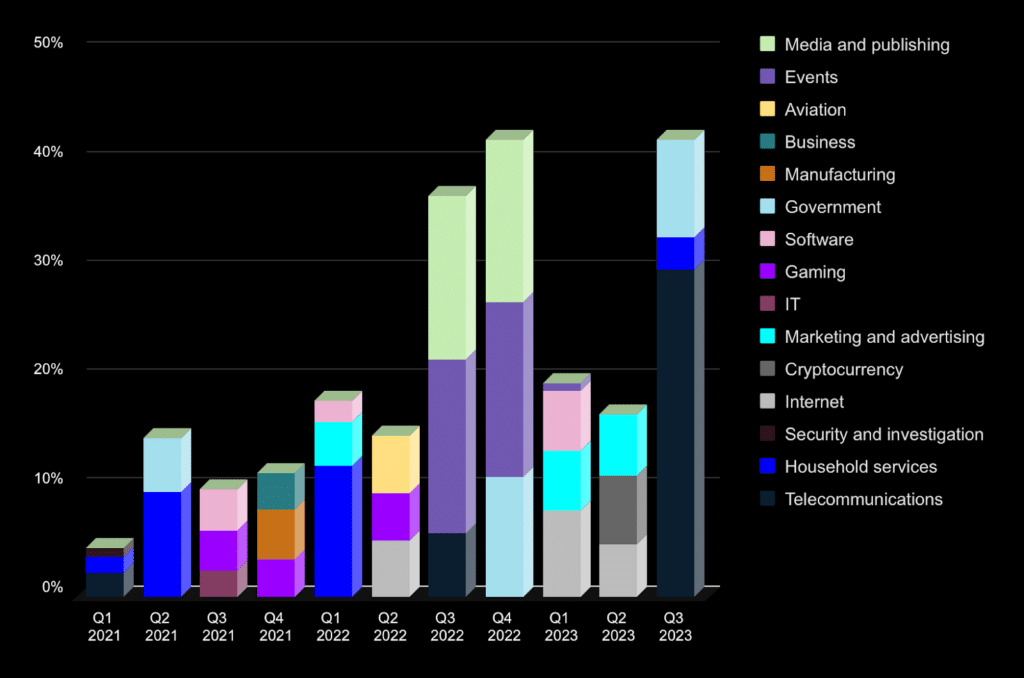
The most targeted industries by DDoS attacks for the quarters of 2021 to 2023
In contrast to industries, the most targeted countries are clearly visible. The top ones were the United States and China, and then there is the same diversity as with industries. We’ve illustrated the three most attacked countries for each quarter from 2021 to 2023.
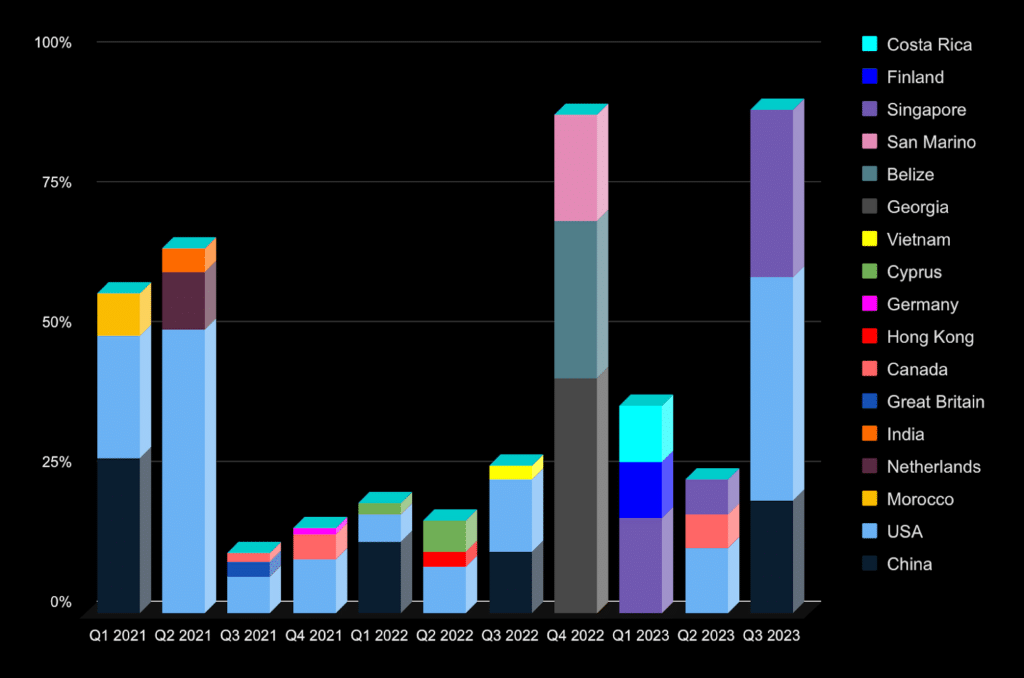
The most targeted countries by DDoS attacks for the quarters of 2021 to 2023
The number of DDoS attacks consistently increases from 1.3 to 1.6 million annually over the last 5 years. Therefore, the projected number of DDoS attacks in 2024 is expected to reach approximately 2 million.
How to counteract DDoS attacks? Our proven method over the past years involves implementing basic protection, application-level protection, testing all layers of defense through simulating various attacks, and adjusting the protection based on the results of this testing.
Forecast for 2024
The virtual space remains a hub of constant challenges and opportunities. As a result, cyber attacks, extortion, and data breaches are gaining momentum, becoming issues for both individuals and large organizations. Data protection and system security should be top priorities for each of us.
Being informed means being prepared. That’s why we’ve compiled the most up-to-date information on incidents and trends, analyzed the threats and attacks of recent years, and made forecasts for the issues and solutions for 2024:
- The number of cyber attacks will increase by at least 15%. Attacks aiming to obtain confidential data will rise by at least 18%, totaling about 2000 attacks. The average cost of data breach will reach at least $4.5 million USD.
- The number of ransomware attacks will increase due to the emergence of new vulnerabilities, creating new opportunities. Additionally, new large groups of ransomware application developers will be organized. Based on trends from previous years, the predicted number is up to 70-75 groups.
- Phishing attacks will aim at espionage and system access. Phishing attacks will grow due to the use of already stolen credentials and artificial intelligence, enhancing and personalizing attacks. These factors will make phishing attacks more effective, less noticeable, and, the most important – more frequent. Financial institutions will be the main targets for phishing attacks in the coming year, with channels including email, social networks, and SaaS.
- DDoS attacks and phishing attacks will increase amid the unstable geopolitical situation globally. DDoS attacks will disrupt the operations of communication, municipal, transportation, financial, and other state institutions. The projected number of significant DDoS attacks in 2024 will be approximately 2 million.
- Cybercrime will also rise due to planned elections in the U.S., U.K., and India. This situation will serve as an opportunity for various types of cybercrimes aimed at creating an unstable environment and disrupting the democratic process.
- Cybercriminals will focus on new targets – cloud resources of artificial intelligence and cryptocurrencies. GPU farming will become a popular target in the field of cloud cyber attacks.
- The priority will be the use of artificial intelligence, both by cybercriminals to develop new attacks, and by organizations for cyber defense.
- To gain access to large target organizations, cybercriminals will continue to exploit not only vulnerabilities in the security systems of these organizations, but also vulnerabilities in their small and large suppliers. An important need for organizations will be to strengthen security tools, processes and protocols, especially in the area of supply chain protection.
- Organizations will focus on the development of cyber resilience in order to quickly recover and minimize data loss, because it is impossible to be 100% protected from a cyber attack. The cyber insurance market will continue to evolve.
- An essential aspect of every organization’s work will be employee training to prevent cybercrimes.
Every company needs to prioritize information security. It sounds clear and obvious. At the same time, based on our experience, we can say that the systems and data of many organizations remain very vulnerable.
If you’re unsure whether your information security system is ready for the challenges of 2024, we invite you to get a real security check through penetration testing. During such assessments, we almost always identify critical vulnerabilities, unauthorized access possibilities, data leaks, or operational disruptions. Contact us today, and we’ll be happy to help!
_______________________________
Subscribe to our x.com page, so you don’t miss our new publications.
