The problem of password memorization and its solution
Understanding the trends of securing the “digital doors” to systems and utilizing modern authentication methods is key to ensuring strong protection of not only military, financial or medical data, but also any intangible assets. The loss of these assets can be detrimental not only to the government or business, but also to a multitude of ordinary computer and smartphone users.
Traditional methods of using passwords are slowly dying out as modern computing power for hacking far exceeds the ability of humans to memorize strong passwords. This poses serious challenges to the security of access to a multitude of systems because personal and corporate data protection depends on this security.
This article will provide security professionals with useful tips on how to raise awareness among users and software developers about the importance of strong passwords, password protection tools, and other methods related to authentication. At the same time, the article will be of interest to a wide range of readers: from users and system administrators to IT managers and systems analysts.
How hackers crack passwords and why this is possible

To understand the logic of hackers, it is worth starting with the realization that any rules that make it easier to remember passwords also make it easier to reveal them. That is the ways in which passwords are created simultaneously shape the ways in which they are guessed.
Let’s consider this principle as an example of the most popular password creation patterns and methods of password selection.
- Numbers in a row — “1234”, “123456”, “87654321”. It is surprising that in the 21st century, there are still systems that do not prohibit the creation of such passwords. They are extremely popular because of their ease of memorization, but are just as easy to crack.
- Popular words are ”password”, ”unknown”, ”admin”, and ”user”. They represent a category of passwords usually associated with basic or administrative functions, or are generic, default, or common terms that are often used for convenience.
- Keyboard and letter sequences — “qwerty”, “asdfgh”, “abcdef”. These are simple sequences of characters that are easy to memorize and quick to type on the keyboard. Their order is determined by the neighboring keys of the QWERTY keyboard or alphabetical order.
- The combination of numbers and letters is “abc123”, “a1b2c3”, “password1”. These sequences are a bit more complex than simple sequences of letters or numbers. They combine alphabetic and numeric elements. This at first glance may give the impression of greater security. However, they are also quite predictable and are often used by users.
- Simple numeric combinations are “123123”, “111111”, “020202”. They are easy to remember due to their repetitive structure. Each of these passwords contains several identical parts, which makes them convenient for users, but at the same time vulnerable to hacking.
- Common phrases are “letmein,” “iloveyou,” and “welcomehome.” Although these are technically passphrases that should be more secure than single words, they are too simple and popular phrases that are often used in everyday life. They are based on popular expressions or emotional statements, which help users to memorize them easily and attackers to anticipate them easily.
- Personal names — “ashley”, “michael”, “robert”. Users often use personal or popular names as passwords because of their ease of memorization and emotional connection. However, such passwords are very vulnerable to hacking because names are easy to anticipate or find in dictionaries or other publicly available sources.
- Years and dates — “13011990”, “2007”, “19Sep1985”. There are advantages to using these passwords as they are easy to remember due to the personal significance of the dates, but at the same time, they can be easily guessed by attackers if the dates are known. Even if not, they are relatively easy to pick up.
- Brand or company names — “Google2023”, “Apple123”, “Samsung!”. Passwords consisting of names of well-known brands or companies are chosen by users because they are recognizable and easy to remember. Although such passwords may seem individualized, their popularity makes them easily predictable and vulnerable to dictionary attacks.
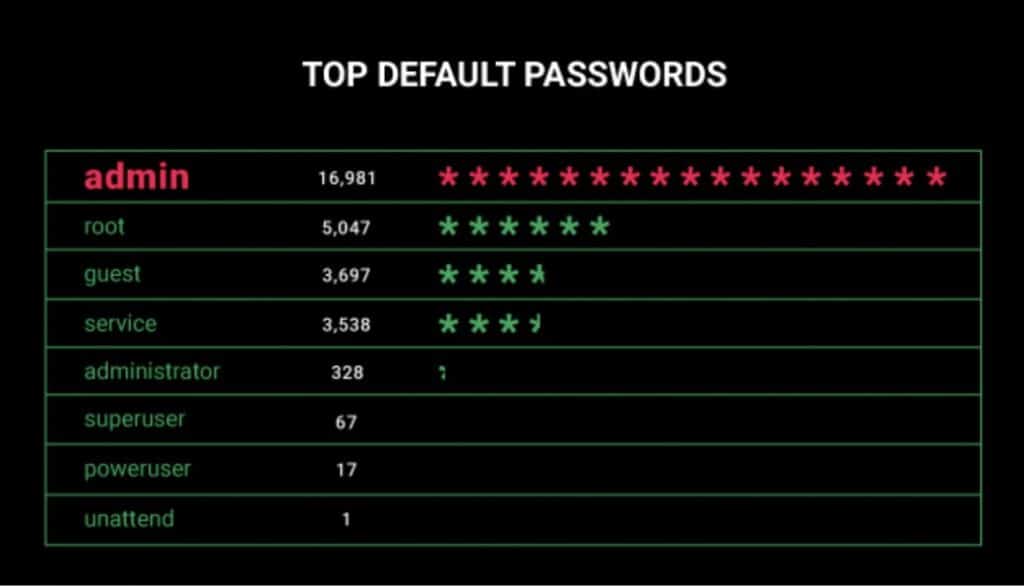
Causes of password problems
So, we’ve looked at the basic patterns for remembering passwords and at the same time realized that any patterns underlie the development of password-cracking techniques. But is this the only cause of the problem?
Knowing the reasons why weak passwords still exist will allow security professionals to better manage risk and create more targeted educational programs and policies. These causes, or rather factors, can be divided into several major categories:
- Human and cultural factors:
- Ease of memorization.
- Minimization of effort.
- Lack of awareness.
- Lack of education.
- Social norms.
- Attitudes toward security.
- Technical causes:
- Inadequate system design.
- Lack of support for password managers.
- Lack of multi-factor authentication or other methods.
- Psychological factors:
- Illusion of security.
- Overestimating the ability to protect accounts.
- Underestimating the methods of hackers.
- Postponement to the future.
- Organizational and economic factors:
- Company policy does not establish strict password requirements.
- The organization does not invest in training for its employees.
- Incorrect risk assessment (balance of losses and benefits, false perception of hacking risks).
Weak passwords remain popular due to a combination of human, cultural, technical, psychological, organizational and economic factors. Robust data protection and account security is the result of not only technological solutions, but also the conscious actions of users and developers.
Modern methods of hacking and data abuse require constant attention and adaptation. Therefore, it is worth actively improving your knowledge and implementing new security methods and tools. Only a comprehensive approach will ensure reliable protection in the digital world.
Password Hacking Techniques

Password hacking is one of the most common threats in cybersecurity. Apart from simply picking password variants, there are several other, more sophisticated hacking methods. Below is a detailed overview of the six main methods used by hackers to compromise passwords.
This information will be useful to software developers, system administrators, and information security professionals. At the same time, regular users can also gain useful insight that will improve their password protection.
1. Social Engineering
Social engineering is about manipulating people to obtain sensitive information, including passwords. Key approaches include:
- Using persuasive stories or arguments.
- Using authoritative roles (tech support, management).
- Exploiting trust and psychological weaknesses.
For example, a hacker calls a company posing as a tech support employee. He informs the target that suspicious activity has been detected in his account and he urgently needs to change his password. The hacker asks for a current password to “verify identity” or sends a fake form to be filled out.
Our company conducts realistic phishing simulations to raise awareness and prepare staff for such threats. This helps to identify vulnerabilities and increase the level of protection.
2. Brute force attacks
A brute force attack involves automatic trying of all possible combinations of password characters until the correct password is found. Key features:
- Use of powerful computers for fast tries.
- Use of software tools such as “John the Ripper” or “Hashcat” (popular password cracking tools).
- High probability of picking short passwords.
For example, a hacker uses specialized software that automatically generates and enters millions of possible password combinations. The program starts with the shortest and simplest passwords, gradually moving to more complex ones.
The table below shows the time it takes to crack passwords with a brute force attack, depending on the length and complexity of the passwords. The upper left corner is the weakest password, and the lower right corner is the strongest password.
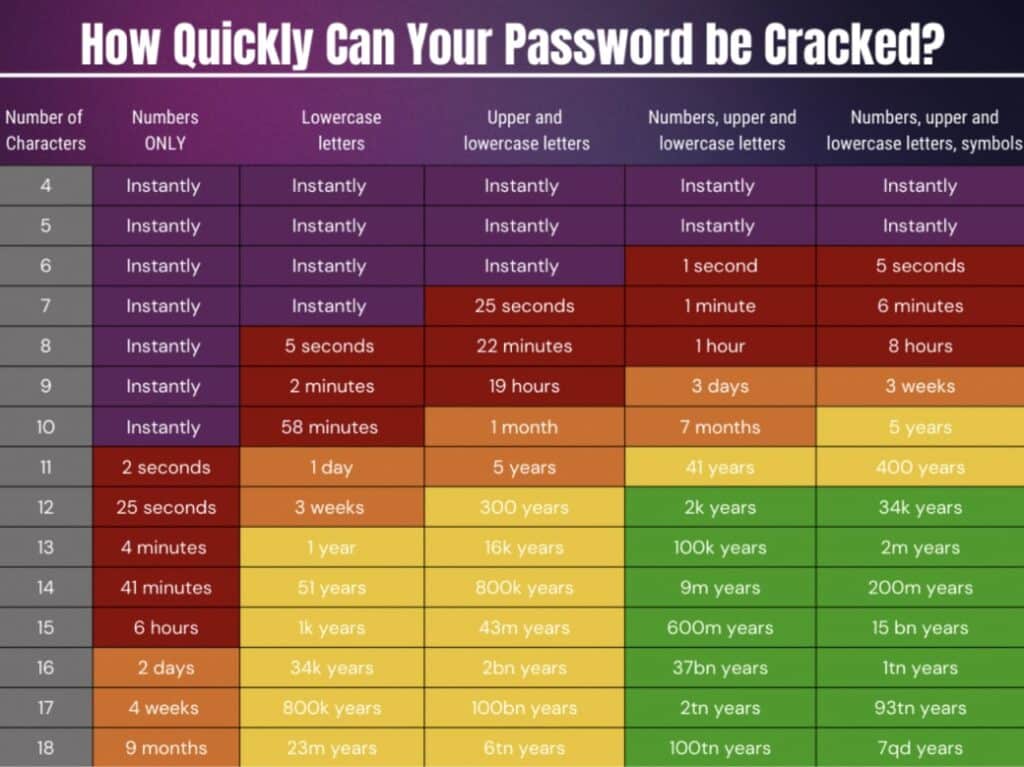
This table shows not only the importance of complex and long passwords, but also the specific relationship between password complexity and password length. This relationship is due to the time a hacker spends to crack a password using the character brute force method.
3. Dictionary attacks
A dictionary attack uses pre-collected lists of the most common passwords that people often use. Actually, this is the selection of well-known words that we wrote about above. Here we should describe this attack from a technical point of view and note the technical features and advantages of this attack:
- Use of large databases of common passwords.
- Higher speed compared to brute force attacks because the number of combinations is much smaller.
- Greater effectiveness against accounts with simple or popular passwords.
For example, a hacker uses a password database (“dictionary”) containing all known words of all languages and millions of known (including previously cracked) passwords starting with “123456”, “password”, “qwerty”, etc. The program automatically substitutes these passwords for the victim’s account until it finds the correct one.
4. Rainbow table attacks
Rainbow tables use pre-calculated hash function values to quickly find matching passwords to which some weak hashing algorithms used to create password hash codes have been applied. This makes the password-cracking process much faster than brute force attacks, while yielding more password variants than dictionary attacks. Key aspects:
- Use of pre-computed hash tables.
- Preparation of large amounts of data including millions of possible password hashes.
- Efficiency when using standard hash functions such as MD5 or SHA-1 without “salt”.
For example, a hacker has access to a database of password hashes. Instead of searching through all possible password combinations, the hacker uses a rainbow table to quickly find a matching password based on its hash. This greatly speeds up the hacking process, as calculating hashes in advance avoids re-calculation during the attack.
5. Keyloggers and spyware
Keyloggers and spyware (spy software) are designed to track and record a user’s keystrokes in order to obtain passwords. Key steps:
- Utilizing malware to stealthily install on the victim’s computer.
- Continuous tracking of the user’s activity.
- Sending the collected data to the hacker for further use.
For example, the hacker installs a keylogger on the victim’s computer through malware that may be downloaded along with a freeware program or through a phishing site. The keylogger records all keystrokes, including passwords, and forwards them to the hacker.
6. Combined attacks
Combined attacks involve using different methods to crack passwords and obtain sensitive information. These attacks increase the efficiency and speed of cracking by uniformly searching for weaknesses of different types (low character variety, low character count, presence of words in the password, etc.). Features:
- Combining direct and indirect password acquisition methods to improve efficiency.
- Application of automation of processes related to password acquisition (mailings, phishing, spyware, direct attacks on passwords).
- Using adaptive algorithms that change strategy depending on the results obtained.
Examples of such attacks include:
- Social engineering + keyloggers (luring to a malicious website and stealthily installing spyware).
- Phishing + brute force attacks (collecting information and using it to hack).
- Dictionary + pattern attacks (using dictionaries and popular patterns, such as birthdates and names), and more.
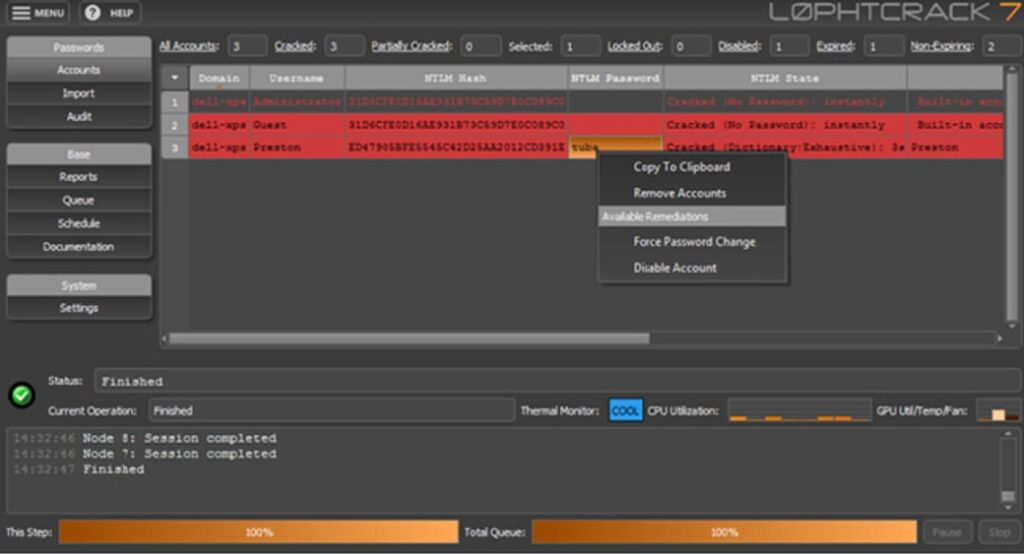
Below is a screenshot of L0phtCrack, a popular tool for implementing combination attacks.
Protecting against password hacking requires an awareness of existing attack methods and the application of appropriate security measures. A strong password is still the primary protection of your personal information in the digital world. It is recommended that you create passwords that are at least 12-16 characters long, use a variety of character types, and avoid obvious patterns and personal information.
Unique passwords for each account and changing them when you feel risk can greatly increase security. Random word phrase passwords are easy to remember and difficult to crack. To solve the problem of difficulty in remembering such passwords, it is worth paying attention to the use of password managers that create and store complex passwords, greatly simplifying the process of security management. Let’s take a closer look at them.
Password managers

What is a password manager and how does it work?
A password manager is a specialized software or service designed to create, store and manage user passwords in a secure manner. Password managers store passwords in encrypted form and prompt or semi-automatically enter them when logging into websites or applications for convenience and security.
How a password manager works:
- Password generation. Password managers can automatically create complex random passwords. Users can customize the length and complexity of passwords, including the use of uppercase and lowercase letters, numbers, and special characters.
- Password Storage. Passwords generated or entered by the user are stored in encrypted form in the password manager database. To access this database, a master password or a composite authentication method (e.g. pin code + biometrics) is used.
- Automatic form filling. Password managers can automatically fill out login forms on websites. This simplifies the authentication process and reduces the risk of phishing.
- Synchronization between devices. Many password managers support the synchronization of data between different devices. This allows users to access their passwords from any device connected to the Internet.
Let’s look at examples of such tools, and their advantages and disadvantages.
Popular password managers
- Google Password Manager is a built-in password manager for many Google services. This manager is mostly known for its use in the Chrome browser. Google Password Manager offers the generation of complex passwords, supports automatic form filling, synchronization of passwords through your Google account, password protection with encryption and easy access to saved data through your browser.
- LastPass. One of the most popular password managers that offers free and paid versions. It supports password generation, password storage, automatic form filling, cross-device synchronization, multi-factor authentication, note storage and AES-256 encryption.
- 1Password. A well-known password manager with a high level of security. Offers family, individual and corporate plans with support for multi-factor authentication and synchronization between devices. Supports auto-fill forms, AES-256 encryption, Touch ID and Face ID, and integration with various platforms.
- Bitwarden. Open-source password manager with high security and a free basic version. Supports password storage, automatic form filling, cross-device synchronization, AES-256 encryption, and multi-factor authentication.
- Dashlane. Password manager with an intuitive interface and extensive features including VPN, automatic form filling and darknet monitoring.
- Keeper. A secure password manager that offers additional business features including password management for teams, integration with enterprise systems, security reports, SSO and LDAP integration.
In summary, password managers increase the level of protection for personal and corporate data, simplifying the password management process and improving the overall security of users on the Internet.
At the same time, you should keep in mind that password managers, like any complex software, sometimes have technical vulnerabilities. Also, you may lose your master password for your password manager. Such events can compromise or destroy all your passwords. That is, compared to memorizing passwords in your head, password managers create the risk of a new point of failure. Therefore, you should use these applications and services with caution.
They can be used as standalone tools or they can be part of multi-factor authentication. For the sake of completeness, should tell a little more about it.
Multi-Factor Authentication (MFA)

What is MFA?
Multi-factor authentication (MFA), specifically two-factor authentication (2FA) or two-step verification, is a method of protecting access to accounts and systems that requires a user to provide two or more independent proofs of their identity. MFA greatly increases security because an attacker must have not only a password but also other authentication factors to gain access.
How does MFA work?
MFA uses a combination of several authentication factors, which may include:
- Something you know (such as a password or PIN).
- Something you have (such as a phone, smart card, or token).
- Something that is part of you (e.g., biometrics: fingerprint, facial or iris recognition).
When a user tries to log in, they first enter their password. The system then requires an additional authentication factor, such as a code sent to a smartphone or a fingerprint scan. Only after successfully passing all the authentication steps, the user is granted access.
Types of multi-factor authentication:
- SMS codes — the code for authentication is sent to a cell phone. This method of obtaining the second factor was historically one of the earliest, but modern security standards do not consider it reliable enough anymore due to vulnerabilities in mobile networks.
- Mobile applications — special programs for generating one-time codes.
- Biometrics — using a user’s physical characteristics for authentication, such as a fingerprint, facial or iris recognition.
- Hardware tokens — physical devices that generate one-time codes or connect to a computer (e.g., YubiKey).
- Email codes — authentication codes sent to the user’s email.
- Push notifications — a notification is sent to the user’s mobile device and the user has to confirm the login by pressing a button, and sometimes also by selecting the desired button from several.
It is important to consider that smartphones, which are often used to obtain MFA codes, can also be targeted. Attackers can carry out an attack by hacking into the smartphone or SIM card. To minimize these risks, the following measures should be followed:
- Setting a strong password to lock your smartphone.
- Regularly updating its software.
- Using anti-virus software and firewall.
- Protecting your SIM card with a PIN and a contract with your mobile provider or registering your ID card with your provider.
- Enabling smartphone tracking and locking features in case your smartphone is lost or stolen.
- Paying close attention to suspicious messages or calls that may be a social engineering attempt.
MFA is an important tool for securing accounts and systems, providing an extra layer of security and protection against many types of attacks. Using multiple authentication factors makes it tens and hundreds, if not thousands, of times harder for attackers and provides better data protection for both individual users and organizations.
General advice for security professionals regarding authentication security

Given the importance of passwords in protecting personal and corporate data, specific steps must be taken to improve the strength of those protections. Here are a few key recommendations:
- Promote the use of complex and unique passwords and policies to secure them, such as implementing password generators, CAPTCHAs, or limiting the number of password attempts.
- Implement strong password managers and rules for their use. Manage the risks of users compromising and losing the password manager’s master password.
- Implement multi-factor authentication, single sign-on (SSO) technologies and modern Identity and Access Management (IAM) solutions, tools and techniques.
- Utilize information security training programs for users and software developers.
- Conduct regular audits of systems and the entire organization, including assessing the correct behavior of users and system administrators.
- Regularly update your own cybersecurity knowledge and skills.
Implementing these measures will help significantly improve account security and protect data from unauthorized access, leakage, destruction, tampering and corruption.
At the same time, don’t just stop there. Look for new approaches to improve security while reducing costs. For example, utilizing SSO technology can simplify resource access management while reducing the risks associated with multiple passwords and inappropriate system access.
Another example is passwordless authentication. Instead of passwords, in some cases, biometrics (fingerprints, facial recognition), one-time passwords, or email or SMS links can be used. This increases security or improves the user experience by reducing the need to remember complex passwords.
Finally, optimize the cost and user inconvenience associated with authentication. For example, contextual and adaptive authentication uses contextual information to make access decisions, including user location, device type, access time, and behavioral factors. Adaptive authentication can increase or decrease authentication requirements depending on the identified risk, such as requiring additional proof of identity for suspicious activities.
We, like other world-class cybersecurity experts, are actively working to promote a culture of security and raise awareness among users and software developers to ensure that personal and corporate data is well protected. Therefore, we can assist you with security assessments, penetration tests, incident investigations and training to improve the security of your systems, as well as many other information security tasks.
Using promo code “IAM”, book a free consultation today on the security of your accounts, authentication and access mode, or any other cybersecurity issues.
