Information security in 2024: what cybersecurity skills and certifications are required for a successful career
Information security incidents continue to increase in 2024. The field of information security is becoming more dynamic and complex. Professional development, cybersecurity certification, understanding of required skills are important not only for beginners, but also for CEOs of companies in various industries, HR departments, professional development specialists, etc. If you’re looking for practical information to help you get a cybersecurity job, or to find the professionals you need to protect your organization or your business, then you’ve landed on the right page. Welcome to the dynamic world of cybersecurity in 2024, where skills and knowledge are the currency of success.
What does modern cyber security consist of?
Cybersecurity domains serve as specialized areas where professionals hone their skills in a particular area of cybersecurity to strengthen a specific layer of digital defenses. These domains help build a roadmap for entry-level engineers, consultants, and professionals looking to navigate the wide range of jobs in this dynamic field.
Use the domain map to understand the structure of the areas, determine the direction to take, and what skills to develop for your chosen industries. Such a map is important for all types of businesses that use IT. It helps understand what to focus on when choosing an outsourcing company or cybersecurity experts. It is also necessary for cybersecurity professional development specialists, as it gives an understanding of what should be taken into account when developing programs for each domain. A simplified example of such a map is here.
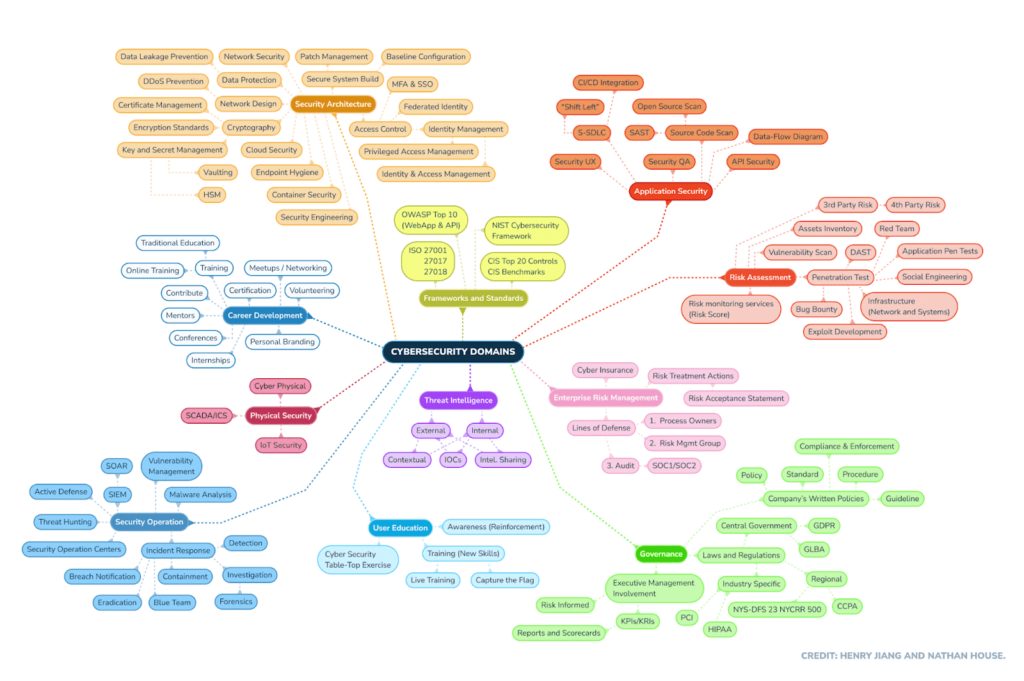
Source: www.stationx.net
Many competencies from different domains are strongly related to each other. Some competencies are on the borderline of different domains, or are repeated in various fields with different specifics. Let’s explore the cybersecurity domains of this map in detail.
Security architecture
The foundation of a secure digital environment is built by security architecture. Professionals in this field design and implement an overall framework that defines how security controls, protocols, and technologies are integrated. From network architecture to secure application development, security engineers create resilient frameworks that withstand a multitude of cyber threats. The core competencies required for a security architect include knowledge and experience in the following disciplines:
- Network security;
- Cryptography;
- Identity and access management;
- Security protocols;
- Application security;
- Operating system security;
- Cloud security.
These competencies in combination give security architects the ability to create comprehensive, resilient security architectures that protect organizations from a wide range of cyber threats.
Application security
Professionals specializing in application security focus on designing and building secure software, as well as identifying and fixing vulnerabilities in the software code. This ensures that applications are resistant to malicious exploitation. Starting from building secure coding processes to regular audits, this area is crucial to reducing the risks associated with the ever-changing application landscape. Application security includes the following elements:
- Secure coding practices;
- Programming languages;
- Web application security;
- Security frameworks and libraries;
- Threat modelling;
- Security DevOps (DevSecOps) – this specialty is at the intersection of Application Security with Security Operations.
These competencies allow application security professionals to prevent vulnerabilities in software applications at the early stages of design, as well as to identify, assess, and reduce them.
Risk assessment
Understanding and mitigating risk is the basis of effective cybersecurity. The field of risk assessment is where this process begins. Risk professionals identify potential threats, vulnerabilities, and their possible impact on an organization’s assets. By conducting a thorough risk assessment, cybersecurity teams can prioritize mitigation and strategically allocate resources. Core competencies in cybersecurity risk assessment include:
- Risk management systems;
- Vulnerability assessment, including penetration testing;
- Quantitative and qualitative risk analysis;
- Business Impact Analysis (BIA);
- Ability to produce quality reports.
These competencies enable cybersecurity professionals to systematically evaluate and manage risks, providing organizations with the information they need to make evidence-based decisions about their cybersecurity posture.
Enterprise risk management
Enterprise risk management involves integrating cyber risk prevention measures into an organization’s overall risk management strategy. Professionals in this area work with various stakeholders to align cybersecurity objectives with business goals. The core competencies required for cybersecurity risk management include the following:
- Risk management systems;
- Business and industry knowledge;
- Security standards and compliance;
- Ability to apply various resources and strategies to manage risks;
- Strategic planning;
- Incident response planning.
These competencies, combined with strategic thinking, entrepreneurial skills, and a comprehensive understanding of the organization’s risk, enable professionals to effectively manage cybersecurity risks at the enterprise level.
Security governance
Strategic security management focuses on establishing and maintaining robust cybersecurity policies, procedures, and structures. Professionals in this field ensure that security measures are aligned with the organization’s business goals, legal requirements, and industry standards. This area provides the strategic direction needed for effective cybersecurity management. Key competencies and knowledge include the following:
- Fundamentals of corporate and security management;
- Compliance with regulatory requirements;
- Risk management;
- Security policies and procedures;
- Security metrics and reporting;
- Supplier risk management.
These competencies enable strategic cybersecurity management professionals to establish and maintain a robust corporate cybersecurity management framework. They ensure that an organization’s information security practices are aligned with its overall business and regulatory needs.
Threat intelligence
Threat intelligence involves the collection, analysis, and interpretation of information about cyber threats. It is the youngest branch of cybersecurity that aims to identify future problems long before they become an attack or incident. Professionals in this field provide organizations with practical knowledge that allows them to take proactive measures to protect against new threats and vulnerabilities. Key competencies required for threat intelligence include:
- Cyber threat landscape;
- Threat intelligence analysis;
- Network protocols;
- Programming and scripting;
- Open-source intelligence (OSINT);
- Dark Web knowledge;
- Cyber Threat Intelligence Platforms (TIP).
These competencies help threat intelligence professionals proactively identify, assess, and respond to potential cybersecurity threats.
User education
As human factors remain an important element of cybersecurity, the field of user education is an important one. Specialists in this field develop and implement programs to educate users about cybersecurity best practices, potential risks, and the importance of following security rules. By developing a culture of cybersecurity, organizations can significantly reduce the risk of exploiting user-centric vulnerabilities that are often exploited by cybercriminals. Cybersecurity user training focuses on preparing an organization’s employees to recognize and mitigate security risks. Key competencies for cybersecurity user training include:
These competencies enable cybersecurity professionals responsible for user training to create a culture of security in an organization, reducing the risk of user-related security breaches.
- Cybersecurity fundamentals;
- Developing security awareness training;
- Communication and presentation skills;
- Knowledge of the threat landscape;
- Understanding human behavior;
- Security policies and procedures;
- Development of exams, tests, and simulations.

Security operations
Security operations is the nerve center of cybersecurity. Specialists in this area monitor security signals, respond to incidents, and ensure the day-to-day protection of an organization’s systems. From identifying threats in real-time to coordinating incident response, the effectiveness of security operations directly impacts an organization’s ability to effectively counter cyber threats. The core competencies that security operations professionals must possess include:
- Security information and event management (SIEM);
- Incident detection and response, including investigation;
- Network security monitoring (NSM, NDR);
- Intrusion detection and prevention systems (IDPS);
- Endpoint security;
- Security analytics;
- Threat intelligence integration and threat hunting;
- Vulnerability management.
These competencies enable security operations professionals to proactively monitor, detect, respond to, and mitigate security threats.
Physical security
Physical security is an extremely important component of cybersecurity, as it focuses on protecting an organization’s sensitive data, physical assets, facilities, and personnel from physical threats. Key aspects of physical security in cybersecurity include access control systems, surveillance, intrusion detection, visitor management; incident response planning; and physical security assessments to identify vulnerabilities. Let’s take a look at the basic physical security competencies:
- Technical competencies (working with electronic security systems, surveillance and intrusion detection, access control technologies);
- Physical security risk assessment;
- Crisis management;
- Understanding of psychology.
A comprehensive approach to physical security strengthens the overall cybersecurity posture by anticipating and addressing vulnerabilities in the material world. It complements digital security measures to ensure the integrity of the defense strategy.
Career development
As the cybersecurity industry evolves, specialists need to continually improve their competencies. Career development includes developing strategies for ongoing learning, training, and professional development. This includes keeping up with new technologies, obtaining relevant certifications, and participating in professional development programs. The core competencies required to develop a career in cybersecurity include:
- Training;
- Certifications;
- Personal branding;
- Conferences and other communication;
- Mentoring.
These competencies, combined with soft skills such as leadership, critical thinking, and problem-solving, contribute to a successful and fulfilling career in cybersecurity.
Frameworks and standards
The area of regulations, standards, and frameworks establishes the guidelines and benchmarks that organizations follow in their cybersecurity practices. Professionals in this area work with standards such as NIST, ISO/IEC 27001 and CIS Controls to ensure that cybersecurity measures are in accordance with industry-recognized standards. Compliance with these standards provides a structured approach to cybersecurity, increasing consistency and efficiency. Key knowledge of cybersecurity professionals in the context of frameworks and standards include the following:
- ISO/IEC 27001;
- NIST CSF (Cybersecurity Framework);
- CIS Controls;
- PCI DSS;
- GDPR;
- ITIL (Information Technology Infrastructure Library);
- CMMC (Cybersecurity Maturity Model Certification).
These competencies ensure that organizations implement robust and effective security measures tailored to their specific needs and regulatory requirements.
All domains of cyber security play a crucial role in strengthening defenses against a variety of evolving cyber threats. Are you choosing your own path in the information security field, or planning to integrate cybersecurity measures in your company? You need to understand both hard and soft skills – professional competencies and business qualities. We’ll take a closer look at the different types of skills needed for cyber security below.
The essential hard skills for a cybersecurity career
Hard skills, or professional skills, are the foundation on which reliable defenses against cyber threats are built. The ability to navigate the complex web of programming languages, network protocols, and the latest technologies is a must for cybersecurity professionals.
The list of required cybersecurity skills is extensive, as there are many cybersecurity domains. This does not mean that you need to know all of them and be able to do everything. To become an information security specialist, you need to choose the areas of your interest and develop the skills needed in that area. Alternatively, you should analyze your existing solid skills and then choose the best field. So, let’s find out what are the hard skills for cybersecurity!

Cloud security
Cloud security competency is becoming increasingly important as organizations migrate to cloud environments. Cybersecurity professionals with cloud security expertise understand the unique challenges associated with cloud platforms such as AWS, Azure, or Google Cloud. This includes data protection, cloud security assessments, securely configuring cloud infrastructure, and implementing strong access controls in cloud environments.
Risk assessment, analysis, and management
Cybersecurity professionals need to be skillful in the area of security risk. Risk assessment involves identifying potential threats and vulnerabilities, analyzing their possible impact, and quantifying the risks associated with them. The ability to assess and manage risks is crucial for making informed decisions, prioritizing security measures, and allocating resources efficiently.
Governance, risk management, and compliance (GRC)
GRC focuses on establishing and maintaining robust governance structures, managing risk effectively and ensuring compliance with relevant regulations and standards. GRC specialists are involved in developing policies, defining risk management strategies and assuring that cybersecurity measures comply with legal and industry requirements.
Penetration testing
Penetration testing, or ethical hacking, is a proactive approach to identifying and addressing security vulnerabilities. Professionals in this field simulate cyberattacks to assess the effectiveness of existing security measures. Penetration testers use a combination of technical skills, dedication, intelligence, creativity, and strategic thinking to identify potential weaknesses and provide recommendations for improving the overall security system.
Security analysis
The ability to conduct a thorough security analysis is an important skill for cybersecurity professionals. This involves assessing the security posture of systems, applications, and networks using techniques such as vulnerability assessment and risk analysis. Security analysts must identify potential weaknesses, evaluate their impact, and recommend mitigation strategies to strengthen the overall security architecture.
Security engineering
Security engineering involves the development and implementation of reliable security solutions. Professionals in this area create systems with built-in security measures, ensuring that cybersecurity is an integral part of the development lifecycle. From the initial secure coding to the creation of a robust infrastructure, security engineering plays a key role in building defenses that can withstand evolving threats.
Artificial intelligence and machine learning
Today’s cyber threats are becoming increasingly sophisticated and complex, and the integration of artificial intelligence (AI) and machine learning (ML) is crucial to identifying and reducing risks. Cybersecurity professionals skilled in AI and ML can use these technologies to analyze large amounts of data, detect anomalies, and improve threat detection capabilities. This skill set is especially important to stay one step ahead of attackers who also use advanced techniques, including AI, to breach security.
Encryption and cryptography
The protection of confidential information relies heavily on encryption and cryptographic methods. Cybersecurity professionals need expertise in implementing encryption algorithms, managing cryptographic keys, and ensuring secure communication channels. Mastery of encryption and cryptography is fundamental to protecting the confidentiality and integrity of data across a variety of digital platforms.

SecOps and incident response
Security operations (SecOps) integrate security measures into daily processes, requiring professionals to monitor and respond to security events in real-time. This involves continuously monitoring security systems, analyzing alerts and coordinating incident response efforts. Professionals with incident response skills can quickly identify, analyze and mitigate security breaches. Creating incident response plans, conducting forensics, and coordinating actions to contain and remediate threats provides a sustainable defense against cyberattacks.
Programming and scripting
At the very core of the cybersecurity technical landscape lies the mastery of programming and scripting languages. Whether it’s automating routine tasks, developing custom security tools, or conducting complex penetration tests, the ability to code effectively in such languages as Python, JavaScript, Bash, or PowerShell is not just a skill, it’s a necessity for cybersecurity. Programming skills allow professionals to create customized solutions tailored to unique security challenges.
Networking
Understanding the intricacies of network protocols and configurations is a must in the cybersecurity industry. Professionals need to decode, decrypt and analyze network traffic, identify vulnerabilities and implement robust security measures to protect against unauthorized access. Whether it’s strengthening firewalls, configuring routers, or performing network forensics, networking skills are fundamental to protecting the vast interconnected systems that characterize the digital landscape.
Operating systems
A comprehensive understanding of operating systems (OS) is fundamental for cybersecurity professionals. Whether securing Windows, Linux or Unix environments, professionals must understand the ins and outs of each OS to identify vulnerabilities, apply fixes and configure security settings. Operating system knowledge is the foundation on which a secure computing environment is built.
Identity and access management
Controlling user access to systems and resources is a key aspect of cybersecurity, and identity and access management (IAM) is at the forefront of it. Identity and access management professionals define and manage user roles, permissions, and authentication methods, ensuring that only authorized individuals, processes, or equipment have access to critical data and systems. This skill helps prevent unauthorized access and maintains a secure digital environment.
Web security
With the increasing use of online applications and services, web security has become an important specialized area of cybersecurity. Web security professionals are experts at identifying and reducing web application vulnerabilities, protecting websites, web applications, frameworks, content management systems, and APIs from common web attacks such as cross-site scripting (XSS), SQL injection, and many others.
Application security
Securing software applications is an important aspect of cybersecurity, and security professionals focus on preventing, detecting, and eliminating vulnerabilities in software code. This involves designing application security, conducting code analysis, implementing secure coding practices, and using tools to ensure that applications are resilient to cyber threats.
The most essential skills in cybersecurity
Cybersecurity professionals and beginners alike are constantly wondering what skills of candidates are of most interest to hiring managers. ISC² conducted such a study and published the results in its report.
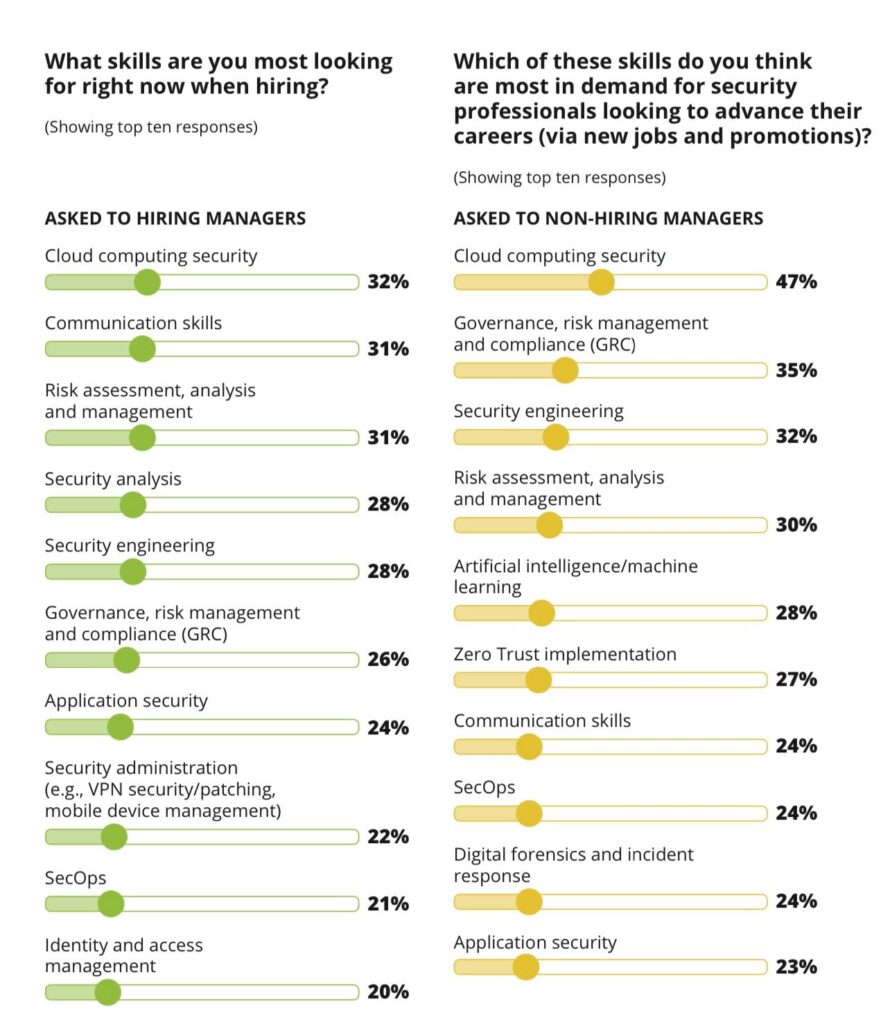
Source: isc2.org
The range of professional skills in cybersecurity is wide and varied. Cybersecurity professionals must constantly update and expand them to stay one step ahead of new threats. Acquiring these technical competencies is a must for those who navigate the multifaceted work environment in various areas of cybersecurity. Beginners should focus on the key skills of their chosen field and develop them. Also, CEOs and HR departments should pay attention to these skills, as the quality and qualifications of their staff affect the security of their business.
Looking for reliable partners to ensure the security of your business? Outsourcing and outstaffing is an effective solution today. Reach out to the professionals!
Key soft skills required for cybersecurity professionals
Cybersecurity soft skills are essential for everyone: beginners, professionals at any level, and executives. Soft skills increase not only individual performance but also the overall resilience of cybersecurity teams. Understanding and honing them is not just a recommendation, but a necessity for success in all areas and each professional level of cybersecurity.

Language skills
Fluency and competence in English and other languages is one of the most important soft skills required. Cybersecurity professionals work with international teams, navigate a variety of technical and regulatory frameworks, and often have foreign partners and clients. Being fluent in the language of their team and customers facilitates effective communication with colleagues and clients. A high level of foreign language proficiency enhances global collaboration and ensures that security measures are accurately communicated across language and cultural boundaries. Such language proficiency is a testament to the adaptability of a cybersecurity professional, as effective communication is of utmost importance.
Communication and presentation
Effective written and verbal communication and presentation skills are of prime importance in a field where complex and often quite abstract security concepts are communicated to a variety of stakeholders. There is a reason for the term “security marketing” – the ability to show risks and sell your services, even to an internal client. Cybersecurity professionals must clearly articulate risks, strategies and solutions to technical and non-technical audiences. Employees communicate daily with their team, managers, interns, partners, and customers. Competent written and verbal communication is the key to efficiency, clarity of information for all team members, and time-saving. The ability to provide a precise explanation or clear presentation of certain information, often complex or incomplete, reduces the risk of misunderstanding, ensures a quality result and long-term cooperation.
Productivity
In the dynamic field of cybersecurity, productivity is more than just meeting deadlines and completing tasks. It is the effective management of resources to optimize results. The ability to maintain a high level of productivity guarantees prompt implementation of security measures, timely remediation of vulnerabilities, and fast and effective response to incidents.
Work quality
The effectiveness of cybersecurity measures depends on the quality of work performed by professionals. The problem is that it is not always possible to describe security quality as specific customer expectations. Therefore, in cybersecurity, quality indicators are often set by certain industry standards. Adherence to high quality standards ensures that security solutions are not only effective but also resilient to new cyber threats. The quality of each employee’s work not only shapes their personal image, but also affects the company’s reputation.
Learning ability
Cybersecurity professionals must have the ability to continuously learn and transfer knowledge effectively. Our main goal is to treat our trainees and employees with care. We constantly encourage and help them improve their skills, gain new knowledge, give advice and guidance to maximize their potential.
Work attitude
A positive and proactive attitude to work is the key to a successful career in cybersecurity. Cybersecurity professionals with a positive work attitude are better able to adapt to unpredictable threats, find creative ways to solve problems, and don’t give up when faced with difficulties.
Work independence
Cybersecurity professionals often work in a dynamic and rapidly changing environment, which requires a certain amount of autonomy in decision-making. Independence is especially important when dealing with small security projects or incident response scenarios, where quick and decisive action can mitigate potential damage.
Teamwork
While individual skills are important, cybersecurity is inherently a collaborative field. The ability to work seamlessly in a team is another soft skill in cybersecurity. Cybersecurity professionals need to cooperate with different departments, find compromises, share threat data, and jointly develop strategies to strengthen the security of the organization.
Analytical skills
Analytical skills are the foundation of cybersecurity. Experts need to analyze complex security incidents, attack patterns, and detect malicious activity in huge amounts of data. Strong analytical skills allow cybersecurity experts to identify potential vulnerabilities, predict new threats, and develop proactive strategies to protect against cyberattacks.
Leadership
Every employee should develop leadership skills as they move up the career ladder, because the essence of security is to create solutions to problems, promote these solutions, transfer knowledge, and encourage the use of measures and tools that are not always convenient or understandable. Cybersecurity leaders guide their teams with a strategic vision, make critical decisions during incidents, and influence the tone of the organizational culture. The fastest way to become a leader is to mentor and support junior professionals and colleagues.
Cybersecurity soft skills summary
While hard skills are the technical foundation of cybersecurity, soft skills provide the basis for their effective application. The balance between hard and soft skills is key not only to success in various areas of cybersecurity, but also to flexibility and resilience in an ever-changing landscape.
The human factor plays an important role in the security of any organization. It accounts for 80% of all cyber incidents. Businesses and companies spend huge amounts of money to restore their assets and reputation. Based on our experience, staff training and education play a key role in information security compliance.
We help every business gain the most up-to-date knowledge, avoiding cyber incidents caused by human mistakes. Our knowledge – your security! Contact us and choose the direction of your development!
Cybersecurity certification: the key to professional growth
Certification is a proof of competence and commitment to excellence in various fields. Starting the journey towards certification not only validates your skills, but also opens the door to new opportunities in the cybersecurity industry.
Starting a career in cybersecurity doesn’t always require a certificate, but it has a number of advantages. When it comes to further development in specific areas of cybersecurity, certifications are a very strong demand from employers and customers.
Advantages of certificates:
- Professional recognition. Certificates enhance professional credibility and demonstrate a commitment to continuous learning.
- Career development. Certified professionals often have better prospects for career growth and higher-paying positions.
- Specialization. Certifications allow professionals to specialize in specific areas of cybersecurity, meeting the ever-changing needs of the industry.
- Networking opportunities. Certification communities provide an opportunity to communicate with like-minded professionals and industry experts.
The Security Certification Roadmap serves as a guide that outlines a strategic path for professionals looking to enhance their skills and advance their careers. You can also use a security certification roadmap to better understand the field you can choose, the features and focus of the chosen field, the certification requirements and their variety for beginners, specialists and experts.
Let’s take a look at one of the most popular certification roadmaps. Thanks to this map, you can get information about each certificate, its cost, where to study and take the exam.
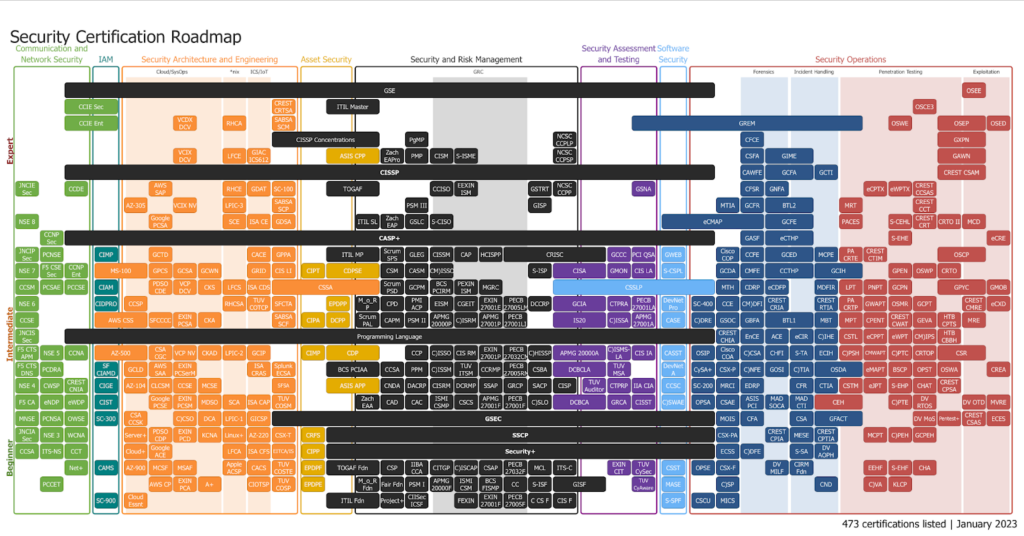
Source: pauljerimy.com
Modern cybersecurity certifications can be divided into the following groups (some certifications are included in several groups simultaneously):
- Communication and Network Security: GSE, CCIE Sec, CCIE Ent, CISSP, JNCIE Sec, CCDE, NSE 8, CCNP Sec, CASP+, JNCIP Sec, PCNSE, NSE 7, F5 CSE Sec, CCNP Ent, CCSM, PCSAE, PCCSE, NSE 6, CCSE, JNCIS Sec, F5 CTS APM, NSE 5, CCNA, F5 CTS DNS, PCDRA, NSE 4, CWSP, CREST CNIA, F5 CA, eNDP, eWDP, MNSE, PCNSA, OWSE, JNCIA Sec, NSE 3, WCNA, CCSA, ITS-NS, CCT, Net+, PCCET.
- Identity and Access Management: GSE, CCIE Sec, CCIE Ent, CISSP, CASP+, CIMP, MS-100, CIAM, CIDPRO, AWS CSS, AZ-500, SF CIAMD, CIGE, CIST, SC-300, CAMS, SC-900.
- Security Architecture and Engineering: GSE, CREST CRTSA, VCDX DCV, RHCA, SABSA SCM, CISSP Concentrations, VCIX DCV, LFCE, GIAC ICS612, CISSP, AWS SAP, RHCE, GDAT, SC-100, AZ-305, VCIX NV, LPIC-3, SABSA SCP, Google PCSA, SCE, ISA CE, GDSA, CASP+, GCTD, CACE, GPPA, MS-100, GPCS, GCSA, GCWN, GRID, CIS LI, PDSO CDE, VCP DCV, CKS, LFCS, ISA CDS, CSSA, CCSP, RHCSA, TUV COTCP, SFCTA, AWS CSS, SFCCCC, EXIN PCSA, CKA, SABSA SCF, AZ-500, CSA CGC, VCP NV, CKAD, LPIC-2, GCIP, GCLD, AWS SAA, EXIN PCSerM, ISA CRAS, Splunk ECSA, AZ-104, CLCSM, CCSE, MCSE, SFSA, Google PCSE, EXIN PCSM, MDSO, SCA, ISA CAP, TUV COSM, CSA CCSK, C)CSO, DCA, LPIC-1, GICSP, GSEC, Server+, PDSO CDP, EXIN PCD, KCNA, Linux+, AZ-220, CSX-T, Cloud+, Google ACE, LFCA, ISA CFS, EITCA/IS, AZ-900, MCSF, MSAF, Apple ACSP, CACS, TUV COSTE, AWS CP, EXIN PCA, A+, CIOTSP, TUV COSP, Cloud Essnt.
- Asset Security: GSE, ITIL Master, CISSP Concentrations, ASIS CPP, CISSP, TOGAF, CASP+, ITIL MP, CIPT, CDPSE, CSSA, EPDPP, CIPA, DCPP, CIMP, CDP, BCS PCIAA, ASIS APP, ASIS APP, GSEC, CRFS, SSCP, CIPP, Security+, EPDPF, TOGAF Fdn, EPDPE, ITIL Fdn.
- Security and Risk Management: GSE, ITIL Master, CISSP Concentrations, PgMP, NCSC CCPLP, ASIS CPP, Zach EAPro, PMP, CISM, S-ISME, NCSC CCPSP, CISSP, TOGAF, CCISO, EEXIN ISM, GSTRT, NCSC CCPP, PSM III, GISP, ITIL SL, Zach EAP, GSLC, S-CISO, CASP+, ITIL MP, Scrum SPS, GLEG, CISSM, CAP, HCISPP, CRISC, CDPSE, CSM, CASM, CM)ISSO, S-ISP, CISA, CSSA, Scrum PSD, GCPM, BCS PCIRM, PEXIN ISM, MGRC, CSSLP, M_o_R P, CPD, PMI ACP, EISM, CGEIT, EXIN 27001E, PECB 27005LM, DCCRP, GCIA, Scrum PAL, CAPM, PSM II, APMG 20000P, C)ISRM, APMG 27001P, PECB 27001LI, IS20, CDP, CCP, C)ISSO, CIS RM, EXIN 27001P, PECB 27032CM, C)HISSP, APMG 20000A, BCS PCIAA, CCSA, PPM, C)ISSM, TUV ITSM, CCRMP, PECB 27005RM, CSBA, DCBCLA, ASIS APP, CNDA, DACRP, CISRM, DCRMP, SSAP, GRCP, SACP, CISP, Zach EAA, CAD, CAC, ISMI CSMP, CSCS, APMG 27001F, PECB 27001F, C)SLO, DCBCA, GSEC, SSCP, Security+, TOGAF Fdn, CSP, IIBA CCA, CITGP, C)ISCAP, CSAP, PECB 27032F, MCL, ITS-C, M_o_R Fdn, Fair Fdn, PSM I, APMG 20000F, ISMI CSM, BCS FISMP, CC, S-ISF, GISF, ITIL Fdn, Project+, CIISec ICSF, FEXIN, EXIN 27001F, PECB 27005F, C CS F, CIS F.
- Security Assessment and Testing: GSE, GREM, CISSP, GSNA, CASP+, CRISC, GCCC, PCI QSA, CISA, GMON, CIS LA, CSSLP, GCIA, CTPRA, PECB 27001LA, IS20, C)ISSA, APMG 27001A, APMG 20000A, C)ISMS-LA, CIS IA, DCBCLA, TUV MSA, TUV Auditor, CTPRP, IIA CIA, DCBCA, GRCA, CISST, GSEC, SSCP, Security+, EXIN CIT, TUV CySec, GISF, TUV CyAware.
- Software Security: GSE, GREM, CISSP, eCMAP, CASP+, GWEB, S-CSPL, CSSLP, DevNet Pro, CASE, CASST, DevNet A, CCSC, C)SWAE, GSEC, SSCP, Security+, CSST, MASE, S-SPF.
- Security Operations: GSE, OSEE, OSCE3, GREM, OSWE, OSEP, OSED, CFCE, GXPN, CSFA, GIME, GAWN, CISSP, CAWFE, GCFA, GCTI, CREST CSAM, CFSR, GNFA, eCPTX, eWPTX, CREST CCSAS, MTIA, GCFR, BTL2, MRT, CREST CCT, eCMAP, GCFE, PACES, S-CEHL, CREST CRT, CRTO II, MCD, CASP+, GASF, eCTHP, S-EHE, eCRE, Cisco COP, CCFE, GCED, MCPE, PA CRTE, CREST CTIM, OSCP, GCDA, CMFE, CCTHP, GCIH, GPEN, OSWP, CRTO, CSSLP, MTH, CDRP, eCDFP, MDFIR, LPT, PNPT, GCPN, GPYC, GMOB, SC-400, CCE, CM)DFI, CREST CRIA, CREST RTIA, PA CRTP, GWAPT, OSMR, GCPT, CREST CMRE, eCXD, C)DRE, GSOC, GBFA, BTL1, MBT, MPT, CPENT, CREST CWAT, GEVA, HTB CPTS, MRE, CREST CHIA, EnCE, ACE, eCIR, C)IHE, CSTL, eCPPT, eWPT, CM)IPS, HTB CBBH, OSIP, Cisco COA, C)CSA, CHFI, S-TA, ECIH, C)PSH, CMWAPT, C)PTC, CRTOP, CSR, CySA+, CSX-P, C)NFE, GOSI, C)TIA, OSDA, eMAPT, BSCP, OPST, OSWA, CREA, SC-200, MRCI, EDRP, CFR, CTIA, CSTM, eJPT, S-EHP, CHAT, CREST CPSA, OPSA, CSAE, ASIS PCI, MAD SOCA, MAD CTI, CEH, C)PTE, DV RTOS, DV OTD, MVRE, GSEC, MOIS, CFA, CSA, GFACT, DV MoS, Pentest+, CREST CSAS, ECES, SSCP, CSX-PA, CREST CPIA, MESE, CREST CPTIA, MCPT, C)PEH, GCPEH, Security+, ECSS, C)DFE, S-SA, DV AOPH, OPSE, CSX-F, DV MILF, CIRM Fdn, EEHF, S-EHF, CHA, C)SP, CND, C)VA, KLCP, CSCU, MICS.
We know how difficult it is for beginners to understand all the things. But don’t worry! H-X Technologies provides and helps to obtain certifications from accredited organizations.
For a better understanding of certification in information security, the following categories of certification can be distinguished:
- Beginner certificates. These certifications establish a basis for understanding the fundamental concepts of cybersecurity. For example, (ISC)² CC, CompTIA Security+, or EC-Council CND.
- Intermediate certificates. Building on the foundational knowledge, the intermediate certificates delve into specific areas such as strategic security, ethical hacking, incident response, and network security. This category includes certifications such as Cisco CCNA, ISACA CGEIT, ISC² SSCP, or EC Council CPENT.
- Expert certificates. For professionals who are looking to develop as deeply as possible in one or several areas, these certifications offer in-depth specialization and the highest level of proven professionalism and experience. This category includes certifications such as GIAC Security Expert (GSE), (ISC)² Certified Information Systems Security Professional (CISSP), CREST Certified Simulated Attack Manager (CSAM), or Offensive Security Certified Expert (OSCE).
Understanding the vector of development and the desire for a successful future are motivating factors for learning. You can take certification training and exams in various organizations. Here are some of them:
- OSCP, OSCE – Offensive Security;
- CC, SSCP, CISSP – ISC2;
- CISA, CISM, CGEIT – ISACA;
- ISO 27001 Lead Auditor, ISO 27001 Senior Lead Auditor – BSI Group or PECB.
Certification of cybersecurity professionals is a frequent requirement (72%) of organizations for employment and professional development. What are the most popular certifications in the world? (ISC)² conducted a survey and obtained the following results.
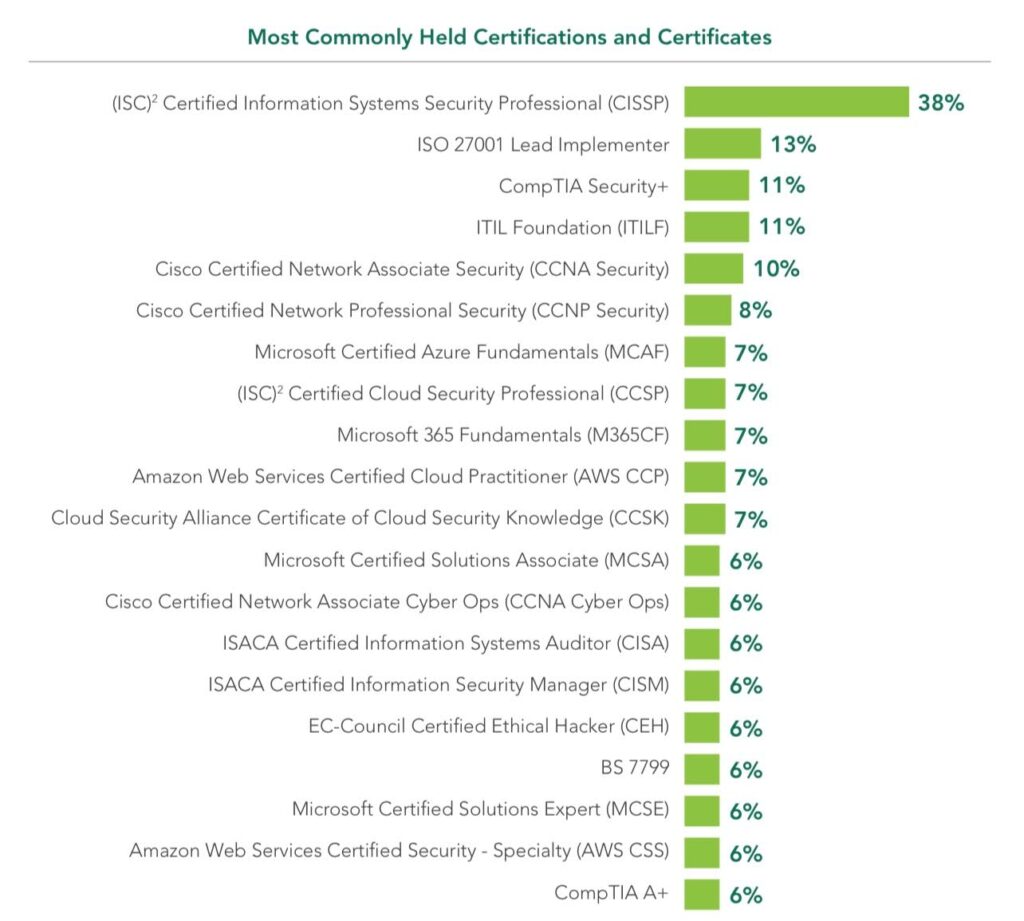
Source: www.isc2.org
Using the security certification roadmap, professionals can strategically choose certifications according to their current knowledge and career goals, ensuring a comprehensive skill set and competitive advantage in the dynamic field of cybersecurity. This map is also used by authors of professional development programs, instructors, HR departments, and company executives to understand the qualifications of specialists and see the vector of development.
Certification is an important step towards obtaining the desired profession, considering that cybersecurity beginners often do not know what exactly is needed and where to go next. Getting a job and determining your further professional development is easy! Just contact us.
Career development at H-X Technologies
To simplify the skills training, especially at the initial stages, we at H-X Technologies distinguish two of the most popular areas of cybersecurity:
- Technical cybersecurity (pentests, investigations, smart contract audits, application security, etc.);
- Information security audit and management (strategic management, risk analysis, user training, compliance, etc.).
Given the importance of these areas, we have developed professional development programs for them. We understand the importance of training, professional development, and the relevance of the skills of each specialist, from interns to experts. Therefore, we help each employee to develop, acquire relevant skills, and grow confidently in our company.
Conclusions
In 2024, cybersecurity is becoming increasingly important for all types of digital businesses, as the number of cyber incidents is constantly growing. To ensure the protection of the company, it is necessary to assemble a highly qualified team. A balanced combination of technical and social skills, as well as mastery of modern standards and cybersecurity certifications, determines success in this important segment.
We have reviewed the main domains of cybersecurity, the key hard skills required, the importance of soft skills for employees of all levels, and the certification types and advantages. Awareness of these issues is important not only for beginners and cybersecurity professionals, but also for HR managers, company executives, and professional development professionals.
For beginners and specialists, we provide internships, jobs, training, and certification at H-X Technologies. We also offer security services (outsourcing and outstaffing), as well as training and staff education for companies of all industries.
We provide business protection at the highest level and share this experience with you.
FAQ
What are the main hard skills required in cybersecurity?
Employers are looking for candidates with skills such as knowledge of network and cloud security, penetration testing, incident response, encryption, and an awareness of security tools and technologies.
Do cybersecurity professionals need to know programming languages?
Yes, programming knowledge is important for cybersecurity professionals, as it helps with tasks such as automation, scripting, and understanding the internal operation of security tools and exploits.
What programming languages should cybersecurity professionals know?
Python, JavaScript, Bash, and PowerShell are commonly recommended for cybersecurity professionals to learn because of their universality and applicability in tasks such as scripting, automation, and tool development.
What soft skills are highly important in a cybersecurity career?
Soft skills, such as English and other languages, communication, presentation, critical thinking, teamwork, and adaptability, are crucial for effective work.
What cybersecurity measures are prioritized for business?
Cooperation with cybersecurity companies (outsourcing and outstaffing), development of security policies and procedures, employee training, access control, regular software updates, encryption, monitoring of security events, and incident response planning are priorities for any business.
How should your business evaluate the cybersecurity needs and implement effective solutions?
Conduct a comprehensive risk assessment, identify critical assets and potential threats, develop cybersecurity policies and procedures, or invest in reliable cybersecurity tools, and consider engaging cybersecurity professionals for a comprehensive assessment and recommendations. We are happy to help you.
—————————————-
Stay tuned for the latest news and updates on our blog, and follow us on x.com.
